您现在的位置是:首页 >技术教程 >Trigger +Pipeline 完整实战案例网站首页技术教程
Trigger +Pipeline 完整实战案例
简介Trigger +Pipeline 完整实战案例
2.4.1 案例环境说明
-
示例项目:http://code.icloud2native.com/root/spring-boot-helloWorld.git
-
触发机制:
- 用户推送代码至项目仓库
- 由Push Hook 自东触发pipeline的流水线的执行
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-6jsyOFls-1684738152154)(imagesimage-20230113164026230.png)]](https://img-blog.csdnimg.cn/9705a1cb52af4d5e84ab0e06d17175d9.png)
2.4.2 项目实现
1、在k8s上部署一个gitlab,前面上节已经完成。
2、运行的任何一个eventlistener的webhook不允许匿名推事件,所以得生成gitlab webhook token的secret: 01-gitlab-token.yaml:
apiVersion: v1
kind: Secret
metadata:
name: gitlab-webhook-token
type: Opaque
stringData:
# Generated by command "openssl rand -base64 12"
webhookToken: "8/MDKoGoabPzFeZr"
3、eventlistener运行为pod的时候,要读取trgger等资源,所以需要授予RBAC : 02-gitlab-eventlistener-rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: tekton-triggers-gitlab-sa
secrets:
- name: gitlab-webhook-token
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: tekton-triggers-gitlab-minimal
rules:
# Permissions for every EventListener deployment to function
- apiGroups: ["triggers.tekton.dev"]
resources: ["eventlisteners", "triggerbindings", "triggertemplates", "interceptors"]
# resources: ["*"]
verbs: ["get", "list"]
- apiGroups: [""]
# secrets are only needed for Github/Gitlab interceptors, serviceaccounts only for per trigger authorization
resources: ["configmaps", "secrets", "serviceaccounts"]
verbs: ["get", "list", "watch"]
# Permissions to create resources in associated TriggerTemplates
- apiGroups: ["tekton.dev"]
resources: ["pipelineruns", "pipelineresources", "taskruns"]
verbs: ["create"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: tekton-triggers-gitlab-binding
subjects:
- kind: ServiceAccount
name: tekton-triggers-gitlab-sa
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: tekton-triggers-gitlab-minimal
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: tekton-triggers-gitlab-minimal
rules:
- apiGroups: ["triggers.tekton.dev"]
resources: ["clusterinterceptors"]
verbs: ["get", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: tekton-triggers-gitlab-binding
subjects:
- kind: ServiceAccount
name: tekton-triggers-gitlab-sa
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: tekton-triggers-gitlab-minimal
4、最后一个task: deploy-task,需要部署到k8s集群,所以该pod需要一定的权限,定义RBAC: 03-task-deploy-to-cluster-rbac.yaml:
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: helloworld-admin
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: helloworld-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: helloworld-admin
namespace: default
5、基于maven构建的cache定义的pvc:
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: maven-cache
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: 1Gi
storageClassName: nfs-csi
volumeMode: Filesystem
6、将该项目所有的task定义在一个文件: 05-task-source-2-image.yaml:
---
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: git-clone
spec:
description: Clone the code repository to the workspace.
params:
- name: git-repo-url
type: string
description: git repository url to clone
- name: git-revision
type: string
description: git revision to checkout (branch, tag, sha, ref)
workspaces:
- name: source
description: The git repo will be cloned onto the volume backing this workspace
steps:
- name: git-clone
image: alpine/git:v2.36.1
script: |
git clone -v $(params.git-repo-url) $(workspaces.source.path)/source
cd $(workspaces.source.path)/source && git reset --hard $(params.git-revision)
---
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: build-to-package
spec:
description: build application and package the files to image
workspaces:
- name: source
description: The git repo that cloned onto the volume backing this workspace
steps:
- name: build
image: maven:3.8-openjdk-11-slim
workingDir: $(workspaces.source.path)/source
volumeMounts:
- name: m2
mountPath: /root/.m2
script: mvn clean install
volumes:
- name: m2
persistentVolumeClaim:
claimName: maven-cache
---
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: generate-build-id
spec:
params:
- name: version
description: The version of the application
type: string
results:
- name: datetime
description: The current date and time
- name: buildId
description: The build ID
steps:
- name: generate-datetime
image: ikubernetes/admin-box:v1.2
script: |
#!/usr/bin/env bash
datetime=`date +%Y%m%d-%H%M%S`
echo -n ${datetime} | tee $(results.datetime.path)
- name: generate-buildid
image: ikubernetes/admin-box:v1.2
script: |
#!/usr/bin/env bash
buildDatetime=`cat $(results.datetime.path)`
buildId=$(params.version)-${buildDatetime}
echo -n ${buildId} | tee $(results.buildId.path)
---
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: image-build-and-push
spec:
description: package the application files to image
params:
- name: dockerfile
description: The path to the dockerfile to build (relative to the context)
default: Dockerfile
- name: image-url
description: Url of image repository
- name: image-tag
description: Tag to apply to the built image
workspaces:
- name: source
- name: dockerconfig
mountPath: /kaniko/.docker
steps:
- name: image-build-and-push
image: gcr.io/kaniko-project/executor:debug
securityContext:
runAsUser: 0
env:
- name: DOCKER_CONFIG
value: /kaniko/.docker
command:
- /kaniko/executor
args:
- --dockerfile=$(params.dockerfile)
- --context=$(workspaces.source.path)/source
- --destination=$(params.image-url):$(params.image-tag)
---
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: deploy-using-kubectl
spec:
workspaces:
- name: source
description: The git repo
params:
- name: deploy-config-file
description: The path to the yaml file to deploy within the git source
- name: image-url
description: Image name including repository
- name: image-tag
description: Image tag
steps:
- name: update-yaml
image: alpine:3.16
command: ["sed"]
args:
- "-i"
- "-e"
- "s@__IMAGE__@$(params.image-url):$(params.image-tag)@g"
- "$(workspaces.source.path)/source/deploy/$(params.deploy-config-file)"
- name: run-kubectl
image: lachlanevenson/k8s-kubectl
command: ["kubectl"]
args:
- "apply"
- "-f"
- "$(workspaces.source.path)/source/deploy/$(params.deploy-config-file)
7、将前面的task定义为pipeline资源:06-pipeine-s2i.yaml:
apiVersion: tekton.dev/v1beta1
kind: Pipeline
metadata:
name: source-to-image
spec:
params:
- name: git-repo-url
type: string
description: git repository url to clone
- name: git-revision
type: string
description: git revision to checkout (branch, tag, sha, ref)
default: main
- name: image-build-context
description: The path to the build context, used by Kaniko - within the workspace
default: .
- name: image-url
description: Url of image repository
- name: version
description: The version of the application
type: string
default: "v0.9"
- name: deploy-config-file
description: The path to the yaml file to deploy within the git source
default: all-in-one.yaml
workspaces:
- name: codebase
- name: docker-config
tasks:
- name: git-clone
taskRef:
name: git-clone
params:
- name: git-repo-url
value: "$(params.git-repo-url)"
- name: git-revision
value: "$(params.git-revision)"
workspaces:
- name: source
workspace: codebase
- name: build-to-package
taskRef:
name: build-to-package
workspaces:
- name: source
workspace: codebase
runAfter:
- git-clone
- name: generate-build-id
taskRef:
name: generate-build-id
params:
- name: version
value: "$(params.version)"
runAfter:
- git-clone
- name: image-build-and-push
taskRef:
name: image-build-and-push
params:
- name: image-url
value: "$(params.image-url)"
- name: image-tag
value: "$(tasks.generate-build-id.results.buildId)"
workspaces:
- name: source
workspace: codebase
- name: dockerconfig
workspace: docker-config
runAfter:
- generate-build-id
- build-to-package
- name: deploy-to-cluster
taskRef:
name: deploy-using-kubectl
workspaces:
- name: source
workspace: codebase
params:
- name: deploy-config-file
value: $(params.deploy-config-file)
- name: image-url
value: $(params.image-url)
- name: image-tag
value: "$(tasks.generate-build-id.results.buildId)"
runAfter:
- image-build-and-push
8、最后将trigger, triggerbind, triggertemplate定义:07-eventlisten.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerBinding
metadata:
name: s2i-binding
spec:
params:
- name: git-revision
value: $(body.checkout_sha)
- name: git-repo-url
value: $(body.repository.git_http_url)
- name: image-url
value: icloud2native/spring-boot-helloworld
- name: version
value: v0.10
---
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerTemplate
metadata:
name: s2i-tt
spec:
params: # 定义参数
- name: git-revision
- name: git-repo-url
- name: image-url
- name: version
resourcetemplates:
- apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: s2i-trigger-run- # TaskRun 名称前缀
spec:
serviceAccountName: default
pipelineRef:
name: source-to-image
taskRunSpecs:
- pipelineTaskName: deploy-to-cluster
taskServiceAccountName: helloworld-admin
params:
- name: git-repo-url
value: $(tt.params.git-repo-url)
- name: git-revision
value: $(tt.params.git-revision)
- name: image-url
value: $(tt.params.image-url)
- name: version
value: $(tt.params.version)
workspaces:
- name: codebase
volumeClaimTemplate:
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
storageClassName: nfs-csi
- name: docker-config
secret:
secretName: docker-config
---
apiVersion: triggers.tekton.dev/v1beta1
kind: EventListener
metadata:
name: s2i-listener
spec:
serviceAccountName: tekton-triggers-gitlab-sa
triggers:
- name: gitlab-push-events-trigger
interceptors:
- ref:
name: "gitlab"
params:
- name: "secretRef"
value:
secretName: gitlab-webhook-token
secretKey: webhookToken
- name: "eventTypes"
value:
- "Push Hook"
- "Tag Push Hook"
- "Merge Request Hook"
bindings:
- ref: s2i-binding
template:
ref: s2i-tt
9、运行
kubectl apply -f .
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-kx6fet5F-1684738152155)(imagesimage-20230113172916650.png)]](https://img-blog.csdnimg.cn/24228280c821441583ab662604b6d926.png)
10、在gitlab上增加eventlistener的webhook, 取消SSL验证
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-iB0oAxda-1684738152156)(imagesimage-20230113173218082.png)]](https://img-blog.csdnimg.cn/5cd1371f5374446d8afee599921a210e.png)
2.4.3 项目测试
本地修改main分支文件,然后push, 查看tekton的dashboard上是否会触发:
1、gitlab上已经push 到main分支:
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-2732L9UX-1684738503653)(imagesimage-20230113174046921.png)]](https://img-blog.csdnimg.cn/5ba317bc6307464da130f8d6d72b7966.png)
2、查看是否触发tekton的pipeline执行
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-35tgfFOV-1684738503656)(imagesimage-20230113174154178.png)]](https://img-blog.csdnimg.cn/7e19fb2925c749c7a74982756bd8d3c1.png)
3、查看dockerhub以及kubernetes是否部署成功
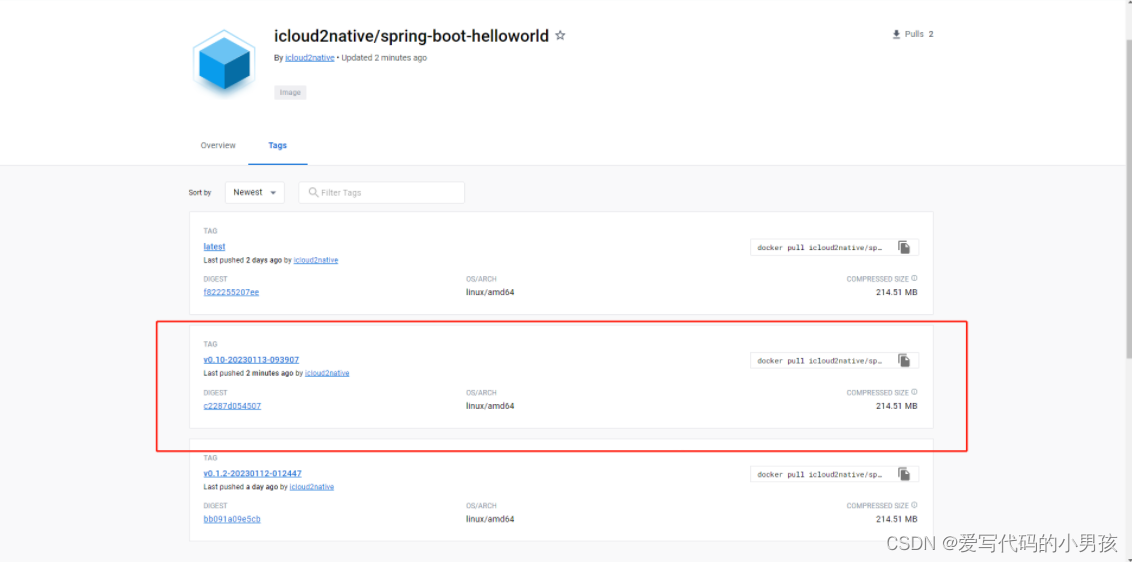

未完待续 。。。
风语者!平时喜欢研究各种技术,目前在从事后端开发工作,热爱生活、热爱工作。






 QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。...
QT多线程的5种用法,通过使用线程解决UI主界面的耗时操作代码,防止界面卡死。... U8W/U8W-Mini使用与常见问题解决
U8W/U8W-Mini使用与常见问题解决 stm32使用HAL库配置串口中断收发数据(保姆级教程)
stm32使用HAL库配置串口中断收发数据(保姆级教程) 分享几个国内免费的ChatGPT镜像网址(亲测有效)
分享几个国内免费的ChatGPT镜像网址(亲测有效) Allegro16.6差分等长设置及走线总结
Allegro16.6差分等长设置及走线总结